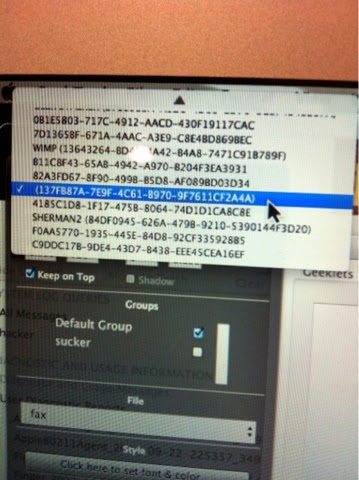
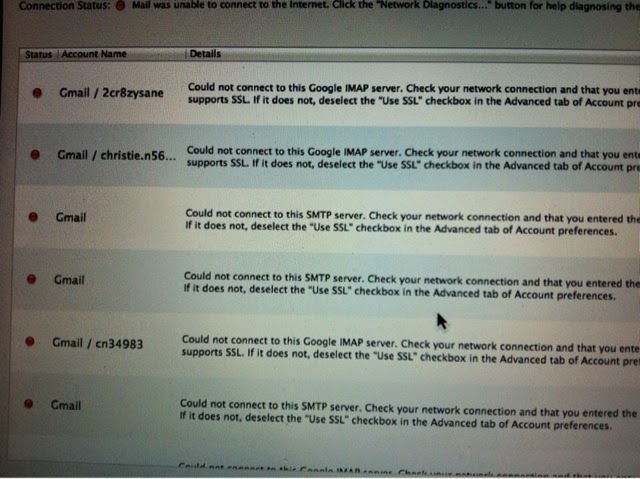
1-26-13
Honestly, ALL the advice I have been given by those who REALLY did understand the extent of what was happening, didn't work. I can't wrap my head around the 'logic' when it's anything but 'logical', what I believe is a network of people, (FBI thinks it's someone I know - so that makes it okay?) but although the extent of the insanity seems more personable, I think it's a much bigger picture and I have my theory that is so out there, but have had since April of 2010 to make reason out of nothing but 'CRAZY' and someone's obsession to play me like a "virtual" game piece of continuous CYBER bullying, which I will keep to myself until I hopefully am able to finish a book. WHY? WHO? If I knew the 'WHO' it would shed a whole lot of light but the FBI isn't willing to help me solve... WHY? Why would every law enforcement that we pay our tax money to, to protect us, too eager to close my case AFTER 'Sherman' appeared on my Apple MacBook Air 1 1/2 years after his 1st appearance on the Dell that seemed to have wiped out ALL it's identification that I had used NUMEROUS times when calling into Tech Support; 'Sherman' appears and my Dell no longer exists? How would 'Sherman' know to be waiting for me at my parent's house or for that matter at 2 different libraries that were about 50 miles away from each other? WHY ME? Which is what I should name my book... "StalkedByHacker WHY ME?" Why did it take me over 4 months to be able to create a Twitter account that has been suspended 5 X's, most recently last night WHILE I was in the middle of tweeting to over 6500 people about being remotely accessed at the 1st library? This time my support ticket isn't being acknowledged at all. Last time I had to have my sister submit the ticket because 'Sherman' prevented me from being able to submit a Support ticket from my iPad. I have ALOT of WHYs! I don't think anyone really wants the answers to. Reality? My Reality has been far from REAL ever since I noticed someone was toying with my Dell laptop that was obviously "possessed" and I still have to this day. It has never been turned on since I took flight to my parent's house in fear for my life because after being on my home LAN line for HOURS giving me the the total run around from the carrier I had at that time because I noticed I was connected to a public network etc. BOTH my LAN line and cell phone had no service when I woke up, and fled to the police station trying to explain hysterically that 'Sherman' was on my Dell laptop and had no service through VW w/ my cell (that was also 'possessed') OR my LAN line that was provided by Comcast and when I had fallen asleep, all I remember was watching my laptop erase pixel by pixel after technical support had 'helped' me... Didn't go over too well acting hysterical but their resolution was to go to www.ic3.gov and report the hacker to get ANY help and almost 3 years later. I guess ALOT of big "HOWs"? Come into play. So many insane, almost delusional events have happened ever since. Plenty happened previous... ALL on line with my DELL, LAN line AND cell. HOW? Was a hacker(?) able to remote access my LG ALLY Smartphone (I had replaced it w/ the old 'possessed' one I watched, literally, the analog clock on the front change to digital and my Text messaging had totally changed formats on me, which I found weird but not per say 'crazy' just thought it odd and when I called VW support regarding it I was told "Someone HAD to have replaced the SIMS card that was in it to have had made such drastic changes" which was absolutely ludicrous. But you get whatever knowledge Support has to offer, in hopes to 'reground' your thoughts of "I must be going crazy" but the best resolution and seemed I guess logical to whoever I spoke with, whether it was Technical or Customer support that whatever 'event' I had just experienced, whether it was my computer or cell is "That's not possible", pretty much casting my own insecurity of questioning my sanity. Be told that enough times by different people who are the "KNOW IT ALLS" and you start questioning your "Reality" - FACTS that you find no logic but yet was REAL and questionable sanity becomes your reality. BUT then God ALWAYS has a way a having the right person you cross paths with that give a FULL BLOWN REASON and explanation to their best ability that helps you find your footing AGAIN. Time and time again. Some more HOWs, if you have the answer by all means 'share' because I have more WHYs? And HOWs to twisted events that no one should have to endure without getting a resolution to resolve the BIG MYSTERY. After the police (after my 1st of numerous approaches to law enforcement) instructed me to report the initial crime to www.ic3gov, HOW was 'Sherman' able to remotely access my LG ALLY smartphone and control every aspect of what I could do and couldn't do? Was free the 1st, about 20 days I owned it, but 'Sherman' was able to LOCK me out from my pattern code I needed to do to use my phone and ALWAYS after store closing hours, then would magically work by the time VW would open. HOW was he able to literally control anything I tried to submit to support for help and turn Chinese? HOW was he able to compromise my cell some how, some way ex: zapping battery life even when plugged in BUT NEVER happen when I took it into VW... He was setting me up to seem "CRAZY" although I had learned after the police station incident, nothing gets resolved when you act IRRATIONAL no matter how FUCKEN IRRATIONAL the situation is. A true test of my sanity. HOW was he, no matter how many times I erased & restored to default, change my phone numbers (that was everyone's favorite resolution to fixing my COMPUTERS, LG ALLY CELL, IPADS, IPHONES etc.) which all it did was erase ANY proof that possibly could have been helpful and did not deter 'Sherman' especially w/ my 1st smartphone. I had it replaced, after changing the numbers too many times to keep count, my VW account was screwed up and after replacing my cell 2 times already, and someone controlling it, I forget what whacked out thing it was doing but ironically I was sent to a Retailer VW (since VW was sick and tired of me w/ my what even seemed to me, UNREAL stories) where for the 1st time it actually did whatever 'Sherman' normally would do to have it back to 'normal' mode (Coincidence? Or being in a brand new VW - RETAILER store have anything to do with Sherman Not being able to continue his charade?) Also - I had long since started taping paper over the camera lense cuz it seemed he could see me and when others were around. Started taking the batter out of it at night so he would stop invading my privacy and would send me bogus articles or have you tube waiting for me to open up, which I NEVER did! Plus for the 1st time I was able to show how it continuously gave me BOGUS errors of not letting me access websites like I was previous to making the mistake of inputting one of the 1st email addresses, that had very important info, that was confiscated when my Dell got hacked ex: My Benefits Resource page or any emails on the web etc. So anyway they were more then happy to replace my cell a 3rd or 4th time at this point but only after they WIPED out my VW account I had had ever since I owned a cell and make a brand new account with a FICTITIOUS name, in case 'Sherman' happened to have some sort of inside resource he had access to, AND change my number to a FL exchange even though I lived in MD at the time. That should, you would think, have taken care of it, at least with my cell. I failed to mention the numerous attempts I had made with my cell to report the hacker to www.ic3.gov since I had not been able to w/ a brand new laptop 'Sherman' took a snapshot of, even having a brand new modem/router I had replaced, too, at home, 2 libraries and my parent's house - all failed attempts because SHERMAN took control of the mouse. Except w/ my ALLY I was finally able to populate www.ic3.gov, input the HELL I had been subjected to, but was NEVER able to submit, just kept populating what I call BOGUS errors that I got way too familiar with these past (almost) 3 years. I was finally able to 7/5/10, 3 months after SHERMAN appeared & the police had instructed me to. My daughter in law who lived about 1 1/2 away from me used her iPad and submitted my story for me, my 2nd attempt of SOMEONE TO PUT A STOP TO ALL THE CRAZY UGLY that at that point, since has been my what seems 'delusional' reality that I could not escape from. All I know is the 3rd or 4th ALLY replacement seemed to do work. No more remote accessing, I had the 1st Brand new laptop replaced, although that was a battle in itself. I had only used it a couple days more after getting THAT new modem/router replaced since, I'm assuming, SHERMAN some how compromised it also. After using the brand new laptop about, 15 minutes of using it, it was like a big FLASH went off. I believe I had McAfee at the time (not that ANY antivirus helped) but it clearly said there had been 2 unsuccessful entries made but the 3rd one WAS successful and that was when the modem/router stopped working altogether. Again, Coincidence? Had the address out of NJ somewhere. When I attempted to print out the details of the report, my printer stopped working. Couldn't save it to a CD because that was one of the many things 'Sherman' corrupted, purposely so I would not be able to establish any evidence. Of course, this is all hindsight. Looking back there's so much more that makes sense now. It all seems so unreal trying to remember everything, but want people to know the seriousness and invasion that has taken place ever since I 1st noticed in February or March of 2010 that my Dell was acting 'possessed' and I was too naive to ever imagine my world would completely change. I moved to FL with another brand new Lenovo laptop, printer, and I thought, an LG ALLY cell that I had escaped the wrath of 'Sherman' from. There's more to the story, obviously is meant for a book with more detail. I was just hoping for a happy ending. I guess there are just too many HOWs? but most of all WHO? And WHY? Usually money's the root of evil... so. I do believe the phone trapping needs to be taken more seriously that I definitely fell pray to. I also believe having a LAN line ties into what I think is a huge elaborate scam that too many people have fallen victim to and don't even realize it. If you have any type of 24/7 tech support or anything that you are paying an amount that seems reasonable... Thinking, thinking, thinking the 3 addresses where 'Sherman' made his presence apparent where numerous cells, printers and computers were compromised ALL HAD LAN LINES AND INTERNET. How many victims are phone trapped today and of course don't know it, but more seriously, WHO? I don't have the answers, I wish I did. But what's most disturbing to me law enforcement agencies need to get it together and stop passing the buck off to another. WHY? Did 'Sherman' make it a point, although, I have my suspicions that privacy no longer exists in our world with technology, but WHY didn't 'Sherman' just stay in hiding like most hackers do? I am a witness to the extreme of how technology is being used when in the hands of EVIL but for whatever reason, wanted me to be quite aware that I was being stalked by a hacker! The few pics are from others on Twitter re: 'my' hacker... & I'm assuming the last one was a message intended for me from 'Sherman' in disguise as Elisabeth, when I was finally able to create my Twitter account, which I will put in separate blog also.