7-11-14 I'm still in total disbelief about it. It doesn't even seem real now. Too crazy! Blocked a lot out. Have to reference to the notes I had kept so diligently at first (after my address was flashed up and down on my screen) but my hand got warn out... REALLY warn out. Surprised I didn't get carpel tunnel. It's hard looking back at the notes I have now. But need to - to write my book. I had even recorded his terrorism at one point (when my wrist had worn out from writing) all the manipulation he was doing on my cell phone (my first smart phone - LG ALLY) after he possessed my normal plain jane cell phone... coincidence? - looking back - who knows - the port holes got burnt out on the old cell but the changes (clock, text messaging format etc.) was told by VW that someone would have had to change the SIMS card & that wasn't possible... (Phone trapped or misinformed?) just like a new modem router I had replaced (cuz I was told the hacker got thru my modem/router) AND 15 min. after connecting a brand new laptop to the brand new modem/router, a big flash went off as if taking a picture of my computer system or something and the port holes burnt out in the modem/router that had just been replaced. Never got it replaced after and bought my first smart phone. That's when the nightmare truly began. I was free from how Sherman totally compromised my Dell laptop, printer, then another brand new laptop (which I returned, but because of how he compromised the new lap top, Office Depot tried to prevent me from being able to return it) from him compromising my very 1st smart phone - LG ALLY for only 20 days. I made the mistake of adding one of the 2 emails he confiscated from me on my Dell into my new cell and would not be free to use any device I used with technology for almost 3 full years... 6 different addresses, 2 different libraries in MD and followed me somehow when I moved to FL even though I had returned the new lap top for a Lenovo laptop that I kept in the box with a brand new printer and had returned my LG Ally cell for the 4th time right before I moved to FL and the compromising had stopped abruptly on the cell so I thought I would be free when I moved from 'Sherman' - my stalking hacker. Only common link was the carrier - VW - that went with me when I moved to FL. Silly me freaked out thinking it was 'identity theft' after 'Sherman' appeared in April 2010 as a user profile who stole admin rights on my Dell and had corrupted my CD drive and the 1st of 4 printers was also corrupted when I tried to use them to have proof of the 'hacking' that my antivirus was able to generate - if only that's all it had been... Identity theft! Apple senior level just told me last week that I may need to change my social security... Basically my identity after I had explained the extent of what the hacker had done. I was told that once already by someone at best but when they had tried to set up my very first iPad for me and was almost not able to, which they said was a first for them that it took as many attempts as it did to activate it. I was unable to activate from my parents house because that was another address that he had totally taken over the computer, printer and phone trapped their phones too! I fell right into that trap! But hadn't even been there in about a year... How in God's name did he know to be waiting for me there? Hindsights 20/20 > he could hear me in my cell. He even recorded one conversation I had with my sister, Jana, which was mostly about what he had done freaky to me that day and sent out conversation to her LAN answering machine that. That's when I lived in MD still and Jana lived in FL ~ freaky!!
Have had ALL my computers (7), printers (4) & numerous cell phones viciously compromised ever since my Dell literally got hacked into right before my eyes over 2 years ago. I was so blind to the nightmare that I would be subjected to, all because I was in total disbelief to what I was witnessing when my hacker named Sherman was hacking his way & ended up taking total control of my devices - ALL because I was too naive to believe this only happens to other people, NOT ME.
Showing posts with label phone trapped. Show all posts
Showing posts with label phone trapped. Show all posts
Friday, July 11, 2014
Saturday, March 17, 2012
Does your Hacker Have A Name?
I would love to know if anyone has been subjected to any part of a Hacker that doesn't stay in hiding and purposely subjects his victims to know they've been hacked by constantly compromising you in ways to torment you. Local authorities, Cyber Crime Unit & the FBI say 'my' hacker is most likely someone I know and definitely is clever enough not to cross the line of breaking any major law for them to pursue. I dealt with the police who in turn referred me to report what I thought was a crime to www.i3c.gov (a lot of good that did - it took me 3 months to accomplish that), was interviewed and they referred me to the FBI in MD. Moved to FL and hacker continued so tried the police there and they referred me straight to the FBI who I had a face to face with but was then told it was a police matter... Felt helpless and like I was running in circles. Apparently 'hacked' victims have to be famous in some way to get help that I have desperately needed to put it to a stop. I thought 'hacking' was illegal; apparently not if you are just an ordinary citizen. Hard to wrap my mind around that hacking & intentionally tormenting someone on their personal computers and cells is okay... More then disturbing! I thought since 'Sherman' appeared a 2nd time on my brand new MacBook Air - I would get the help I needed to put all this crazy tormenting to a stop. I had only owned it for about a month when I got the attention of a senior level by the name of Amanda who seemed genuinely concerned when I had called Apple AGAIN (I couldn't tell you the amount of calls that I had made over a years time frame which I finally realized that I was just getting the run around and they were NOT going to fulfill their promise of replacing my MAC if the issue wasn't resolved. But I did get their attention in Oct. 2011 when I had called to inform them that my Apple ID, which was about the 7th I had created because they continuously were getting compromised where I was unable to use them the way that everyone just takes for granted. The forever password error and this particular day it wouldn't accept my birthday to issue me a new password and read the JavaScript errors to Amanda and filled her in on 'Sherman' and his crusade of taking over 6 PC's by that time, the MAC made it # 7, 4 printers and NUMEROUS cell phones he had hijacked. Took me serious and although this was my 1st MAC and I was not familiar with how it functioned compared to the PCs I had worked my entire career with Verizon Communications, which was C&P Telephone when I started in 1980 on computers.
I had managed to create and save some logs that seemed 'off' to me and had a feeling from the very 1st connection I made that it was being compromised. It all came to a head when Amanda had requested that I email her the logs and the 3 emails I had built into the mail client had been working fine up until that point (could the hacker hear my conversations on my phone?) - I believe so... Too many coincidences that occurred that only by hearing my conversations could the hacker continue to be one step ahead of me > how did he know to be waiting for me at my parents? > how was he able to cyber attack me at 2 totally different libraries that were about 50 miles apart? > how did both my home phone which was connected thru Comcast AND my cell (thru Verizon Wireless) both go dead at the same time after getting the total crazy run around I got the very last time I ever used my Dell laptop and saw it erase pixel by pixel right after seeing my address displayed up and down my screen, as if on a newspaper article when I was living completely by myself and had been given so many different 800 #'s to call to resolve the hijacking of my Dell? > How did the hacker know what article or You Tube that would be waiting for me nearly every morning that had something to do with what I had said or done the previous day on my cell? > How did the hacker have the capability of recording a call I had had earlier in the day with my sister regarding my 'possessed' Dell to only send it to her home line voice mail later that night? It was obvious I was being stalked and he wanted me to know I was in fact entitled to no privacy since hijacking my Dell and my very first cell which led me to buying a new laptop and my first smart phone - the LG ALLY which only led to having absolutely no privacy or the capability of using technology the way it had been intended to.
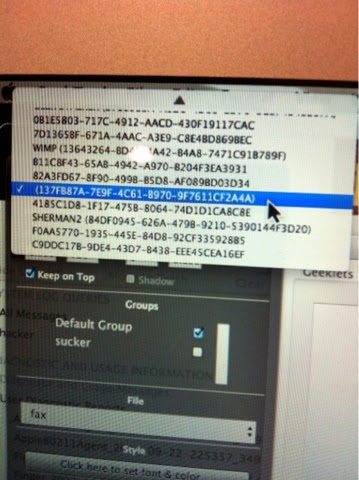
I knew when I tried to email Amanda at Apple the logs I had created and received the message 'password/UN rejected' for all 3 gmails I had built into the mail client, it only confirmed my suspicions I had been trying to ignore that 'Sherman' had some how managed to follow me to another state (I had lived in MD then moved to FL and was at a 4th address that he had relentlessly been stalking me.) Even tried to build in a 4th email thru the mail client which worked until I tried to mail the logs. I was completely blown away! I finally had what I thought would be proof of someone else on my laptop lurking behind the scenes. I had noticed an app that I thought had come with my MAC called the GeekTool App (pictures below) which I had tried to open previous to this just to check it out but had been unsuccessful but for whatever reason made it my mission to open it in hopes it could lead me to some answers. When I finally got it open, I saw 3 sequences of numerous numbers and letters already built in and assumed it was some how what was programming and had been compromised by 'Sherman'. After manipulating the sequences and checking boxes that weren't check and unchecking boxes that were checked it would some how disconnect the hacker from my laptop. I even added more sequences that were equivalent in length of made up numbers and letters in hopes to deter the hacker. (Geek Tool App below)
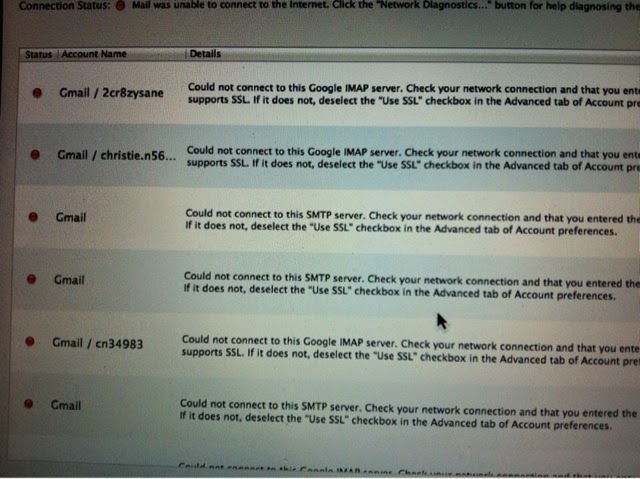
It had a box to name the sequences and I named one WIMP, SHERMAN, SHERMAN 1 etc. and before I knew it they started multiplying rapidly. I figured if I screwed something up that Apple would be able to walk me through how to fix it. Only to find out that this App had NOT been an Apple App and the Geek Squad where I had purchased the MAC (Best Buy) had not put this mysterious App on my laptop at all. It was a total mystery how it was even on my MacBook Air at all. All I know, by manipulating this App I came across some very strange things that were behind the scenes... For one the next picture will show two screens of ALL THE EMAILS that some how ended up on my MAC. You can see the ones I built in had labeled names of the actual gmail I had built so that I could tell them apart. By this time I had accumulated over 100 email addresses in hopes to get rid of the hacker thinking he was able to find me by my email addresses. I just kept creating new ones which wasn't an easy task keeping up with them all and as you can see there were multiple addresses added by the hacker because I certainly had not added them and as you can see were not labeled to the actual address used... But why? You would think someone could give me an answer but that never happened. In fact I'm sure many I spoke with doubted anything I had to say when it came to a 'hacker' hijacking my technology.
By this time I was thrilled that I was able to capture what my eyes were seeing this time around because ALL THE CRAZY I would get subjected on all the other computers would end up so corrupt, I would have no proof of anything. So I really got my hopes up when I reached another senior level at Apple by the name of Erin Elliason who took great interest that an Apple product had in fact been hacked and to a degree that no one could fathom. She was the one who promised to replace my MacBook Air if they were unable to resolve the 'Sherman' I was able to expose for my eyes only (which seemed more then odd that when I took my MAC to Apple for them to get some kind of diagnostic on it, Sherman, as a USER PROFILE with ADMIN RIGHTS could not be seen...) Only at my house but I knew from almost 2 years of torture by that time to take whatever pictures I could because it seemed Sherman always managed to undo anything I would get subjected to when I would take my computer or cell whenever it would act 'possessed' and make me come across as 'CRAZY'. Yep... Sure, UN HUH! It was really getting old trying to explain for example my LG ALLY which got replaced 3 times at one point was having a mind of it's own with the battery charger. It would show a full charge then ZAP no battery life, would plug it in, show a full charge again, unplug and ZAP no battery life but as soon as I took it to Verizon Wireless, not really thinking too much about it except it must be a defective battery and they'll replace it, but it worked fine in the store! They were nice enough to replace the battery but that was the beginning of the hacker toying with my mind in so many different ways that I have blocked out a lot today because it was never ending! Of course, waving my address up and down the screen when I lived by myself was definitely creepy! I do remember the times my cell would do something whacked (example: tried to type in an entry into LG about the hacker and every time I typed it, it backed spaced through every letter typed and delete it) by the time this occurred - I knew the hacker could hear me AND see me whether I was using my phone or not and had caught onto his game so to test my sanity I placed the phone in another room, went to my Step Mother and quietly told her to witness what the hacker was doing, which she did and voila! (I had taped over the camera lense by this time so he couldn't see - learned that the hard way to) she got to witness 'my world of crazy' then purposely said out loud 'watch when I type this entry, it's going to delete each one when I finish' and of course it didn't do it! I knew he could hear me!! He has set me up so often already to prove the actions of someone else on my cell to only look like a fool when it wouldn't do it... Time and time again. I caught onto to his sick, twisted game. When was it going to stop?
Subscribe to:
Posts (Atom)