9-7-12 >>> I am so confused about the twitter account that had taken me more then 6 months to set up. Every time I tried to create it, just like everything else I attempted to do with any device with technology, it got compromised some how, some way. I made numerous attempts, gave up, would wait awhile, try again, of course unsuccessfully, but I KNEW what I was up against. Then for some odd reason, after attempting on and off for over 6 months - I DID IT - I think. I knew nothing about how Twitter worked except I heard about daily from various news sources and it seemed intriguing, but I knew better then to get my hopes up... Why is my stalking hacker allowing me to create a twitter account now? Haven't been able to google search on how to use Twitter but let me give it a shot... I actually succeeded and when I got to the point of entering a User Name, which I hadn't really thought about cuz I had never gotten that far in creating one, but when asked, I didn't hesitate to create @StalkedByHacker & felt victorious to have been able to do that... I was so conflicted - this was probably another 'set me up' by my stalking hacker, who toyed with my sanity for over 2 years.
Seriously, take a moment and really think the next time you attempt to do anything on your computer and it being impossible to succeed whatever it was you were attempting to do... Google search something, create an email account, retrieve your emails, send an email out, try to open up a specific website, change a password, log into a website that does open up, but need to use a UN & password you have just used recently... I could go on and on - let's keep it basic. You are habit of creature and log into your FB account daily to 'share'... You have used the same UN & password for awhile & you go through the motions to get - we'll go with UN and/password incorrect... okay, no biggie, must have a typo somewhere. Try it again. Same error. Really? I know I typed it in right this time but let's do it again... But slower just to make sure I successfully log in, thinking how bad you want to share the most precious picture of an animal you love, maybe that special moment of capturing a precious pic of your child's very first day of kindergarten - or maybe that joyous victory of the child who is all grown up & just graduated from high school ready to go out into the world... Huh? This time a different error - hmmmm. Okay, no big deal. Something's obviously wrong with the site. Will have my 'sharing' moment tomorrow as soon as I get a good night sleep and have my cup of coffee. Happens all the time - right? Must be a 'fluke'. Then you realize that you promised a family member that you were going to email them that recipe you had been promising them forever, so you figure, okay, let me at least get that done before I call it a night. You reopen the email you had already logged into earlier, but for some reason it kicked you out... Log in with the familiar UN & password & some pop up window blocks you from being able to even input your password... Frustrated? Nope, just wish this computer wasn't 'acting' up. And figure, you know what? - I'll just pull up the recipe that I had put in my recipe folder and print it out since I am going to see them tomorrow anyway... No big deal... Really? Can't find the Recipe folder you just went into before you tried to email it to make sure you had the right recipe and NOW you can't find the darn Recipe folder. Okay, let's call it a night. I must be more tired then I thought. I'll just print it out real quick in the morning... The next morning while having your cup of coffee, you decide to print out that recipe... AHA! I knew it, must have been tired, the Recipe Folder was right where I always have it. Send to the printer... Okay now the printer's doesn't want to work! Whatever!! I'll get to it when I get home. So weird, huh? Nope. Weird, odd, disturbing & "coincidences" becomes your way of dealing with a very twisted hacker that gains pleasure of doing this to naive, innocent people all the time. But think about dealing with the above frustrated scenario, day in and day out for over 2 years!! I almost have my sanity back (I think) since my Hacking Griefer seems to have moved on...mmm Stalking? Thru my cell still? Probably then again, maybe not. What's the twisted little phreak gonna do? Don't give a shit. More like (hopefully) he's moved on... Right in front of the big ass truck going 80mph. All I can say is at least now I have a great excuse whenever there is a 'real' fluke while I have my freedom back with technology ... "The Hacker did it" & guess what? I don't give a damn!! Ha! Whatever!! IIWII - Moving Forward. Enjoying technology the way I have been trying to since way before I moved from MD, when 'Sherman' was on the prowl just waiting for just the right person to target... Who's next? I wonder how often the 'twilight zone' I encountered, has been reported by others? I seriously hope the hacker isn't attempting at this moment to make someone else questioning their sanity... I think being able to reverse IP's & zoom in on a hacker's location just might have something to do with my new found freedom. I love Apple!! But what I really want to know is... Why the hell did my Twitter account get suspended? >>>> guess I'll never know when I contacted @support they never really explained why, just that they were sorry & I had to guarantee that I had, in fact, read ALL their rules... Yea... Unhuh - RIGHT!!! My Twitter was out of commission for about 2 full days. I'm up and running again now & think I have around 1,500 Followers... So exciting!!! I was so fricken clueless, but I'm getting there. Follow me on Twitter @StalkedByHacker! And tweet me. Let's ROLL : )))
Have had ALL my computers (7), printers (4) & numerous cell phones viciously compromised ever since my Dell literally got hacked into right before my eyes over 2 years ago. I was so blind to the nightmare that I would be subjected to, all because I was in total disbelief to what I was witnessing when my hacker named Sherman was hacking his way & ended up taking total control of my devices - ALL because I was too naive to believe this only happens to other people, NOT ME.
Friday, September 7, 2012
Monday, June 25, 2012
Don't become a victim of CYBER TERROR
It's something so many people just take for granted... Ahhh being able to share my story after so many failed attempts because I have finally regained (for now) enough freedom to get my story out about a Hacker that has made my life pure Hell. Trust me on this, if it happened to me, anyone's a target to the kind of Hacker that thrives off of causing you nothing but excruciating Grief by compromising everything you use through technology... PCs, Printers, Cell phones, LAN line etc. I have dealt w/ local police, CyberCrime Unit & the FBI in 2 different states in which they all believed the 'unbelievable' actions of a hacker who hacked his way into my Dell laptop in the safety of my home, and they all over sympathized with the Hell I was constantly being subjected to but to my astonishment there was no law the hacker actually broke!?!? Really? I'm pretty sure it's common knowledge that Hacking IS illegal when one obsesses that CYBER TERROR is acceptable in our world today!!? Corrupting every computer and printer you use is controlled by someone else to only corrupt it beyond repair... Can't possibly be okay! I just regret that I LET MY hacker -Sherman- hack his way into my Dell & eventually appear right before my eyes in April 2010 as a profile named Sherman w/ the Chess player icon & stole Administrative Rights, compromised the 2 emails that I was no longer able to access... THEN remote accessed the Dell & shortly after remote accessed my cell which was TOTALLY unacceptable!!! What about my Rights? What if it was you? And sadly it only got worse and the REAL nightmare was just beginning... the CYBER TERROR you could only perceive logical even if exposed to it in a horror movie you would still NEVER believe. Well, all I am trying to do is make people aware that Hacking Griefers do exist and you don't want to be subjected to so much misery that it almost destroys you! LITERALLY. A different form of CYBER BULLYING but with a genius(es) whose mission IS to destroy you to such a degree of questioning your own sanity; your interactions w/ technology will never be same if you let the Hacker gets his way... paranoia will begin to literally suffocate you... Share my story. Although people hear about 'hacking' on the news everyday (and it seems they always 'catch' the bad guy) well I am here to tell you - you do not want to be the one desperately trying to find the right resources that can FINALLY give you back your peace of mind. I utitlized every resource out there to only find out that Hacking Griefers are allowed to invade your life in such an intrusion way that unless subjected to it there is no way for 'others' to understand. Most people take it for granted, the freedom that everyone deserves to have using technology in our rapid growing high tech world unless you have a stalking hacker who gains pleasure thinking their prey is a game piece turned virtual. A bunch of phreaks playing a game, hiding behind technology and invading MY Cyber space since 2010 should be ILLEGAL. Just thank God for Apple and my beliefs... The next 'virtual game piece' may not be so lucky.
Labels:
Arin,
bully,
Connection,
crime,
Cyber,
Cybercrime Unit,
FBI,
Griefer,
hacker,
high-tech,
illegal,
legal,
network,
new technology,
phreaks,
police,
stalked,
Stalking
Saturday, May 26, 2012
The Mystery GeekTool App & My Relentless Hacker
Pictures 2, 3, 4, 5, 6 & 8 - mystery App that no one is claiming to have put on my MacBook Air - The GeekTool App. Other pics show my Hacking Griefer's 'autograph' so boldly added once again as a User Profile on my Mac. When my 3 emails that were already built into the mail client & working just fine generated an error stating 'password rejected' right after I had been asked by an Apple Senior Advisor to send them the 'odd' logs I had created on my new MacBook Air & my network connection had been compromised, I knew for a fact that my hacker HAD been stalking me from my 1st connection and decided fervently to change everything I could in this App. Picture 5 is showing one of the icons I clicked on in this App that exposed 3 property values at first that apparently the hacker had built in (at the time I thought it was a built in Apple App & I knew what I was about to do could possibly whack out my Mac) but I added 3 fictitious values & unchecked everything checked & vis-a-versa then changed ISO Settings to ISO 2022 Japanese but I couldn't believe the property values just kept multiplying! What the hell is going on? By pure luck ALL my emails (over 10) that I was unable to use because of 'wrong UN or Password' populated from ALL devices; iPad, iPhone etc. & I lost ability to do anything because I no longer had Admin Rights on my MacBook Air. I clicked around & stumbled across 'Sherman' as a User Profile which was my Hacker's way of telling me he was still stalking me which I already knew because of all the bizaar encounters I had been having on everything to do with technology since Sherman first appeared on my Dell in April 2010 when I lived in MD. I have since moved to FL when the hacking Griefer appeared a 2nd time as Sherman in October 2011 but has made his presence very transparent until I started dealing with the FBI in MD in August & then shortly after my move from MD to FL in Sept. 2010 again with my LG Android Cell & my then brand new Lenovo laptop which kept acting strangely then getting corrupted time and time again. I thought I would have been safe since the remote accessing of my cell abruptly stopped shortly before I moved from MD. I had already stopped using my Dell completely after watching it delete pixel by pixel while on the phone with 'technical support' one night until about 4:30a.m in April 2010. When I woke up and literally jumped out of bed the next day around 3pm, I went to check my LAN line's VM & caller ID that 'technical support' was supposed to have made a follow up call around 11:00am and saw I had not received any calls and to my astonishment I had no dial tone NOR was I able to make or receive any calls on my cell either. I was completely terrified... in fear for my life. Everything that had led up to the time is incomprehensible. Was it my imagination or did I in fact talk to a REAL 'technical support' from Comcast that kept passing the buck and just made matters worse and never called me the following day. Right before my Dell started erasing, my hacker, named Sherman was in fact waving my present address at the time up and down the side of my screen as if on a newspaper clipping - Really?? Absolutely!!! A scare tactic on the Hacker's part to let me know he knew exactly where I lived... And many more similar haunting stunts. Then I overslept and and I had no way of making a phone call! How could my cell phone AND LAN line both NOT work at the same time? My heart was racing. Too scared to look at my Dell. I had to get to a pay phone or find the closest police station. That's when the reality of finding a pay phone were far and few in between. Hmmmm - I had never noticed that before... But I had never needed a pay phone where I was living before this terrifying incident & what had led up to it. Let me give some advice. Don't EVER go into a police station (or anywhere for that matter) unless you are somewhat composed and can talk rationally. But damn it I truly was in fear for my life. When you get subjected to Cyber Terror the last thing you're thinking is 'act normal' even though the reality as you once knew it, no longer exists and it's very difficult to be rational. At the time I questioned my physical well being. But trust me, I will never forget how I got treated in that police station in the dark of night as if I were same crazed out drug junkie! I was mortified but looking back I should have tried to collect myself a little bit before expecting the police to take what I had to say seriously. When I went to the police here in FL much calmer, the reaction was quite thankfully different. The only information I could get from the police in MD (my very first attempt of numerous attempts going to authorities) was to go on-line to www.ic3.gov and report the crime. No way! Seriously? How much sense did it make for them to tell me to go on-line when I clearly (not rationally maybe) explained amongst being in fear of my life & all the interactions I could think of at that frazzled time including someone was remote accessing my computer & controlling what I could do & not do. A library perhaps... that's another story. What part didn't they get? Just the beginning of 'pass the buck'. I knew after leaving the police trembling (who are supposed to protect but 'whatever'... ) the only place I would have felt safe at would be my Dad's house which was about 40 miles away. Had to find a damn pay phone! Thank God! My Stepmother answered - it didn't go to VM! And they had a computer. All I wanted at that point was to get a good night sleep. I would attempt as soon as possible to go to www.ic3.gov but not that night! BUT... There was only one major problem. The most unimaginable would soon slap me in the face blindfolded! To compound my baffled state of mind... The hacker was waiting for me... No I left my Dell at my house and haven't touched it since except about 3 weeks after my deranged escapade I took one quick glance thinking I would just see a blank screen since it was slowly erasing pixel by pixel when I last had my eyes on it with pure exhaustion talking to Comcast 'technical support'. Still waiting on that follow up call. NOT! But when I glanced at it I couldn't believe what I saw! My entire desktop was covered with newly named folders in alphabetical order and one of them had my X-husbands name on it (his name had kept appearing on my screen really tiny like it was far away in my screen then would float toward me magnifying slowly) Nope. Didn't click on a thing; was shocked to have seen anything at all. Turned it off, closed it and put it in its case - some authoritative figure may want to look at it and has actually been mentioned by CCU but I still have it in the case to this day; untouched since that bizarre encounter. As I mentioned, my hacker the Griefer who goes by Sherman knew somehow I would be attempting to report online the Cyber Terror to Cybercrime Unit from my parent's computer... Would I be able to? No!!! Another blog.
Take all precautions on your computers. Be safe. Don't think it can't happen to you!!! STOP CYBER TERROR!! How in God's name was 'my' hacker able to continue tormenting from my parent's house? How fricken whacked out.. He got into my PC so far away from my parents. No logic exists... The hacker was Stalking me to a degree - no one could imagine.
Take all precautions on your computers. Be safe. Don't think it can't happen to you!!! STOP CYBER TERROR!! How in God's name was 'my' hacker able to continue tormenting from my parent's house? How fricken whacked out.. He got into my PC so far away from my parents. No logic exists... The hacker was Stalking me to a degree - no one could imagine.
Labels:
App,
Apple,
bully,
compromised,
Computer,
Connection,
crime,
Cyber,
Cybercrime,
Dell,
FBI,
GeekTool,
Griefer,
hacked,
hacker,
illegal,
MacBook Air,
new technology,
phreaks,
Terror
Tuesday, May 22, 2012
My Hacker Compromised Network
5-22-12 >> learning more & more about Sherman (my hacker) who gains pleasure tormenting me w/ technology by stalking me & invading my Cyber Space... Stop CYBER TERROR
Journal Entry 10/2011>
Well... Alrighty now - living on little sleep but accomplished something so BIG that was so fricken right there at the click of a button. Got my iPad replaced yesterday. Tried to contact Erin from Apple Technical support - Senior Advisor - left 2 messages & tried calling a couple more times to inform her that the new Sims card did not FIX my iPad (and again, I had so much hope when the AT&T rep replaced my sims card & the 1st thing I had him do was input the email that had prompted all my most recent calls to Apple in addition to an alien seizing my MAC. And it went through, without a hitch. Good sign > new sims card; that was a 1st for my iPad & the one problem seemed to be fixed... Too good to be true - my favorite motto - but had no choice that something new could be the answer to all the mystery (lack of knowledge actually) of getting the error 'wrong UN/password' over & over again ... Errrrrrrrrr - fixed. All the technical support out there with 4 different Internet providers and I - TONIGHT - figured out the 'fix' to that ongoing error I have had for 1 1/2 years now - WOW! Seriously? I'm sure it will be short lived but the more I explore Apple products the more I love them. It is amazing to me with all the 'hacking' you hear out there & how simple it really is to do that I have been subjected to such devastation & total turmoil. Okay so I'm thrilled that I once again stumbled across a mystery to everyone else that I have talked to about the wrong UN/Password issue - one way to fix it... How? My iPhone that has a hotspot connection capability & my wifi printer were not working the way they should... Something did not add up. My brand new iPad was also on at the time & started acting possessed AGAIN - this soon? Think, think, think. Untrusted site/connection when I went into HP printers website on my iPad & then on my iPad - same error. Hmmm mmm. Purely by coincidence I Printed out network status from my new printer & my iPad started acting just like the one I just had replaced last night... SETTINGS > GENERAL > RESET... NETWORK SETTINGS. I stumbled across it on the printer then on my iPad then iPhone and VOILA - the error I have been a victim to & misunderstood by technical support (that's why I believe my calls had to be rerouted with the million of calls I've made to help me make sense of being able to populate an email on the Internet but continued to get the never ending error when putting in the exact info into any mail client... to only create an error that my password was incorrect. Chalked it up to dealing with idiots, rerouted calls, or I was actually going crazy. I just kept questioning myself - with everything I have been through in my past & still managed to keep my sanity - why NOW 50 - 52 years later would I actually become CRAZY? Paranoid... Yes, but for obvious reasons - logical? Absolutely NOT! Does a real Crazy person know their crazy? I don't think so... Although, I most definitely had my doubts at times... But knew better. It would be more sane to believe that I really wasn't sane after all. Ahhhhh... but I am & have to deal with the insanity that has been inflicted on me for so long now. I've actually tried to convince myself that I am crazy so All This INSANITY would make sense... Mission accomplished but need specialists (cyber crime unit?) to help me put all this to an end. The insanity I have been subjected by ‘my’ hacker named Sherman, is the reality that I can't get people who are experts in this field to help me with nor do they understand the magnitude. My current locations have populated over 5 different states besides where my actual location is. This is not one person doing this... Again, I can’t be the only person this is happening to & my story needs to reach out to those that are victims as I am entering this one victory I can put a bandaid on for now but what's next? > Sense writing this I have FINALLY spoke with a very knowledgeable Apple Reps & my Hacking Assault... My Hacker is a Griefer who thrives off of other peoples misery to boost their already over inflated egos! If it could happen to me, it could happen to ANYONE. Too many CyberBullies using technology as a destructive weapon... Please!!
| Created : Oct 12, 2011 11:54 PM | Priority : ★★★★★ | Style : Background7, Font10, Size19 | Tags : alert,connection,network,cyber,FBI,CCUnit,email,Password,arin |
Journal Entry 10/2011>
Well... Alrighty now - living on little sleep but accomplished something so BIG that was so fricken right there at the click of a button. Got my iPad replaced yesterday. Tried to contact Erin from Apple Technical support - Senior Advisor - left 2 messages & tried calling a couple more times to inform her that the new Sims card did not FIX my iPad (and again, I had so much hope when the AT&T rep replaced my sims card & the 1st thing I had him do was input the email that had prompted all my most recent calls to Apple in addition to an alien seizing my MAC. And it went through, without a hitch. Good sign > new sims card; that was a 1st for my iPad & the one problem seemed to be fixed... Too good to be true - my favorite motto - but had no choice that something new could be the answer to all the mystery (lack of knowledge actually) of getting the error 'wrong UN/password' over & over again ... Errrrrrrrrr - fixed. All the technical support out there with 4 different Internet providers and I - TONIGHT - figured out the 'fix' to that ongoing error I have had for 1 1/2 years now - WOW! Seriously? I'm sure it will be short lived but the more I explore Apple products the more I love them. It is amazing to me with all the 'hacking' you hear out there & how simple it really is to do that I have been subjected to such devastation & total turmoil. Okay so I'm thrilled that I once again stumbled across a mystery to everyone else that I have talked to about the wrong UN/Password issue - one way to fix it... How? My iPhone that has a hotspot connection capability & my wifi printer were not working the way they should... Something did not add up. My brand new iPad was also on at the time & started acting possessed AGAIN - this soon? Think, think, think. Untrusted site/connection when I went into HP printers website on my iPad & then on my iPad - same error. Hmmm mmm. Purely by coincidence I Printed out network status from my new printer & my iPad started acting just like the one I just had replaced last night... SETTINGS > GENERAL > RESET... NETWORK SETTINGS. I stumbled across it on the printer then on my iPad then iPhone and VOILA - the error I have been a victim to & misunderstood by technical support (that's why I believe my calls had to be rerouted with the million of calls I've made to help me make sense of being able to populate an email on the Internet but continued to get the never ending error when putting in the exact info into any mail client... to only create an error that my password was incorrect. Chalked it up to dealing with idiots, rerouted calls, or I was actually going crazy. I just kept questioning myself - with everything I have been through in my past & still managed to keep my sanity - why NOW 50 - 52 years later would I actually become CRAZY? Paranoid... Yes, but for obvious reasons - logical? Absolutely NOT! Does a real Crazy person know their crazy? I don't think so... Although, I most definitely had my doubts at times... But knew better. It would be more sane to believe that I really wasn't sane after all. Ahhhhh... but I am & have to deal with the insanity that has been inflicted on me for so long now. I've actually tried to convince myself that I am crazy so All This INSANITY would make sense... Mission accomplished but need specialists (cyber crime unit?) to help me put all this to an end. The insanity I have been subjected by ‘my’ hacker named Sherman, is the reality that I can't get people who are experts in this field to help me with nor do they understand the magnitude. My current locations have populated over 5 different states besides where my actual location is. This is not one person doing this... Again, I can’t be the only person this is happening to & my story needs to reach out to those that are victims as I am entering this one victory I can put a bandaid on for now but what's next? > Sense writing this I have FINALLY spoke with a very knowledgeable Apple Reps & my Hacking Assault... My Hacker is a Griefer who thrives off of other peoples misery to boost their already over inflated egos! If it could happen to me, it could happen to ANYONE. Too many CyberBullies using technology as a destructive weapon... Please!!
| Created : Oct 12, 2011 11:54 PM | Priority : ★★★★★ | Style : Background7, Font10, Size19 | Tags : alert,connection,network,cyber,FBI,CCUnit,email,Password,arin |
Saturday, March 17, 2012
My Hacker At the Library
My connections to the networks I have had in 2 different states, & 4 different addresses w/ 4 different carriers have been compromised by being connected to someone else's network or my connection ends up being connected to a public network, I guess that leaves me open game to the Hacker that continues to intrude my cyber space by subjecting me to such bizarre, almost delusional encounters. My 3rd visit at 2 different libraries, an hour away from each other, I experienced what seems the impossible and if someone else were to tell me both of these encounters happened to them, I don't know if I would believe them. Thank God I had a witness or I would have ?'d my own sanity. Already was by this point in time anyway. There was no logic as to WHO & WHY WAS SOMEONE INTENTIONALLY TOYING WITH ME... WAS THIS JUST A GAME TO SOMEONE? After sharing my story face to face (nothing by phone was sacred at that point in time because of 'phone trapping' - talk about WAY OUT THERE!) to very knowledgeable people with the extent of what a hacker can do (and knew there was such things as 'hackers'; didn't even look at me like I was possessed (believe me, you wouldn't believe the amount of closed minded people that I made a mistake sharing what had become an almost everyday REALITY for me and had the nerve to act like there is no such thing as 'hacking',) who really are idiots and basically do not have enough knowledge to have an intelligent conversation about something you hear about everyday on the news! The 1st library in Baltimore, MD I was trying to go to ic3.gov to submit my hacker story. The local police said they couldn't help me in any way and the only option I had was to go on-line to www.ic3.gov to report the crime that had been committed by hacking, what I thought was illegal. Made numerous attempts to open ic3.gov - just got bogus errors or website got REROUTED to websites that had nothing to do with what I actually needed... When it FINALLY opened, the mouse came to life and went spastic all over the screen; then different screens kept opening to the most bizaare websites so fast I couldn't believe it nor could the person beside me who commented "what the hell is up with your computer?". No sooner did he finish asking me everything closed out & the computer literally shut down. I was in total disbelief and my anxiety was thru the roof! I didn't know what to believe anymore. I had been told (by phone - which became unsafe territory to me that was brought to my attention by someone whose path I crossed, who was knowledgeable about computers and informed me of 'phone trapping' which he fell victim to in a scam that ripped him off financially but never got the chance to give me detail because he was working but warned me to be very careful. From what I had explained to him in regards to there being no logic with ANY phone calls I would make in regards to my computers being controlled by someone in hiding and almost seemed I was being taunted in an evil way. My parents PCs and phone line ended up exactly the same way from the home I fled when I was naive enough to download what I thought was an antivirus but found out the 'antivirus' I had downloaded did NOT exist with Verizon, the carrier that they had and was tricked into seeing yet another fake website that looked so genuine, since I had worked for Verizon my entire career but was so stressed out had forgotten the one antivirus they did offer and the hacker was waiting behind the screens as a customer service rep that I WAS reluctant to interact with when a pop up came up asking if they could be of assistance when I was unable to find anything on their website in regards to an antivirus... 1st clue - it took FOREVER (over 2 hours to download) and in the mist of downloading, get a facetious pop up by the hacker (which I had to come to that realization the day after when I made calls from a payphone to the REAL Verizon who confirmed my paranoia were for reasons that were justified... TOTAL DISBELIEF! Had made a call to the 24/7 'ULTRA tech support' that I think was a total hoax (hindsights 20/20) because looking back was something I ultimately was offered by all 4 different carriers that took your money straight from your bank account (that's what that guy had tried to warn me about but didn't think anything of a $19.95 a month payment that was supposed to give me my sanity back but feel I played right into their hands with what was to come. I believe it was the day before my 1st library attack and I had called from my parents phone (which WAS phone trapped after downloading a hacker's dream come true in order to continue terrorizing me in a way that is still beyond logic. I forget how my parents PC was being compromised but called the $19.95 a month GEEKS that can FIX ALL. The guy asked if he could remote access my PC, which made me feel uncomfortable but had no choice but to trust him. He dove in head first to find 'Sherman' who had obviously at that point taken control AGAIN at a house that I had not been to in over a year but as time went on, realized he was able to hear me on my phone conversations, let alone as I was subjected to even more TERROR was able to hear me, as crazy as this is to absorb but too many circumstances led up to me realizing that if my LG ALLY was within range, he could literally stalk me in ways that I was slow to catch on because how REAL is it that 'Sherman' would and could stalk me literally to an extent that I had to block out once he made a point to be obvious - I had no privacy with my computers (which I picked up soon after he appeared as 'Sherman' on my Dell yet couldn't allow my mind to grasp such an intrusion and WHY?? But now on the very 1st smartphone I purchased after the plain Jane cell I had, acted possessed, which is in another post and the port holes were destroyed... Coincidence? Had a brand new modem/router do the same thing when I thought I was free from 'Sherman' when I had replaced my Dell with a new laptop which only reinforced that 'Sherman' was on a mission. But on the call I made to 24/7 tech, he took charge, remote accessed my parents PC and only heighten my disbelief AND paranoia when he elaborated in such a distressed fashion for my safety. He went on and on to inform me that I WAS IN FACT IN DANGER because with what I had explained the extent of what the hacker had done so far (just touched based actually because my nerves were so raw, and hitting road block after road block knew how skeptical people could be with my REALITY and was concerned about if he would take me seriously or not... But he (REROUTED call I think) emphasized how I needed to fill the police in IMMEDIATELY (already had - no go - dead end) because for 'Sherman' to be remote accessing me, meant he was within 100 ft or yds (I forget which length) and when told that so matter of fact by someone who was a GERU with hackers, put me in more fear for my life! None of it was making any sense! I was in Baltimore in the safety of a home I was living at when hacker first struck and now about 40 miles away in Annapolis, I'm being told the hacker was within 100 ft/yds everytime he remote accessed me? So then that's all I could think and felt like I was losing touch with reality that he was that close to me at this library?
Another clue that I was 'phone trapped' by some organization... But WHY? And WHO could be so cruel - Why ME? So I'm at the 1st library he invaded me (stalking me was becoming more real by the day) and the hacker had taken control of my computer and obviously did not want me to have the capability of submitting my story to Cybercrime Unit. So in addition to remote accessing my computer, then my parents -each time sabotaging me from generating anything to ic3.gov - he could remote access a library computer? No way! This can't be happening!!! I was so shaken up by this invasion. How is it possible that out of about 20 computers in this particular library could my hacker compromise the one I was on? Totally impossible! OR was it? I had recently been told that someone had to be within 100 ft/yds to remote access a computer. WRONG! My hacker was stalking me & on a mission to make me question my own sanity!!! I believe my calls were being rerouted! Too many coincidences to know where I would be and whatever he had me download - IT WAS A WAY FOR HIM TO CONTINUE STALKING ME!! This made it the 3rd location he has remote accessed & taken control of the computer I was on. I remember wondering - is the hacker here?!?!? But decided that's what he wanted me to think. As time went on, I realized I had definitely been misinformed how close a hacker has to be to take control of a computer. 2nd Library location, Annapolis, MD incident - what a doozy - will share on another Blog.
Does your Hacker Have A Name?
I would love to know if anyone has been subjected to any part of a Hacker that doesn't stay in hiding and purposely subjects his victims to know they've been hacked by constantly compromising you in ways to torment you. Local authorities, Cyber Crime Unit & the FBI say 'my' hacker is most likely someone I know and definitely is clever enough not to cross the line of breaking any major law for them to pursue. I dealt with the police who in turn referred me to report what I thought was a crime to www.i3c.gov (a lot of good that did - it took me 3 months to accomplish that), was interviewed and they referred me to the FBI in MD. Moved to FL and hacker continued so tried the police there and they referred me straight to the FBI who I had a face to face with but was then told it was a police matter... Felt helpless and like I was running in circles. Apparently 'hacked' victims have to be famous in some way to get help that I have desperately needed to put it to a stop. I thought 'hacking' was illegal; apparently not if you are just an ordinary citizen. Hard to wrap my mind around that hacking & intentionally tormenting someone on their personal computers and cells is okay... More then disturbing! I thought since 'Sherman' appeared a 2nd time on my brand new MacBook Air - I would get the help I needed to put all this crazy tormenting to a stop. I had only owned it for about a month when I got the attention of a senior level by the name of Amanda who seemed genuinely concerned when I had called Apple AGAIN (I couldn't tell you the amount of calls that I had made over a years time frame which I finally realized that I was just getting the run around and they were NOT going to fulfill their promise of replacing my MAC if the issue wasn't resolved. But I did get their attention in Oct. 2011 when I had called to inform them that my Apple ID, which was about the 7th I had created because they continuously were getting compromised where I was unable to use them the way that everyone just takes for granted. The forever password error and this particular day it wouldn't accept my birthday to issue me a new password and read the JavaScript errors to Amanda and filled her in on 'Sherman' and his crusade of taking over 6 PC's by that time, the MAC made it # 7, 4 printers and NUMEROUS cell phones he had hijacked. Took me serious and although this was my 1st MAC and I was not familiar with how it functioned compared to the PCs I had worked my entire career with Verizon Communications, which was C&P Telephone when I started in 1980 on computers.
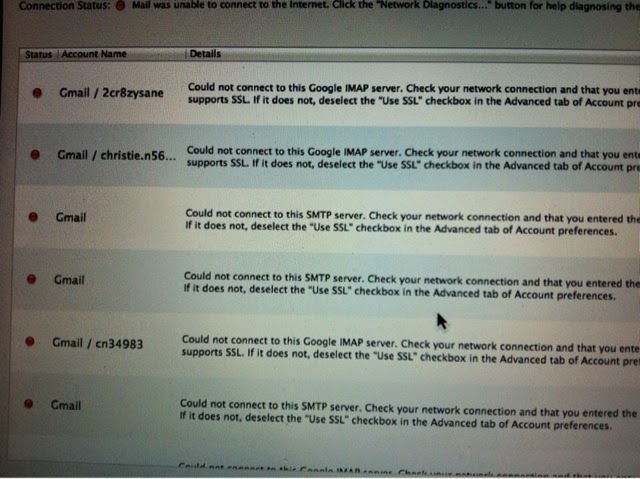
I had managed to create and save some logs that seemed 'off' to me and had a feeling from the very 1st connection I made that it was being compromised. It all came to a head when Amanda had requested that I email her the logs and the 3 emails I had built into the mail client had been working fine up until that point (could the hacker hear my conversations on my phone?) - I believe so... Too many coincidences that occurred that only by hearing my conversations could the hacker continue to be one step ahead of me > how did he know to be waiting for me at my parents? > how was he able to cyber attack me at 2 totally different libraries that were about 50 miles apart? > how did both my home phone which was connected thru Comcast AND my cell (thru Verizon Wireless) both go dead at the same time after getting the total crazy run around I got the very last time I ever used my Dell laptop and saw it erase pixel by pixel right after seeing my address displayed up and down my screen, as if on a newspaper article when I was living completely by myself and had been given so many different 800 #'s to call to resolve the hijacking of my Dell? > How did the hacker know what article or You Tube that would be waiting for me nearly every morning that had something to do with what I had said or done the previous day on my cell? > How did the hacker have the capability of recording a call I had had earlier in the day with my sister regarding my 'possessed' Dell to only send it to her home line voice mail later that night? It was obvious I was being stalked and he wanted me to know I was in fact entitled to no privacy since hijacking my Dell and my very first cell which led me to buying a new laptop and my first smart phone - the LG ALLY which only led to having absolutely no privacy or the capability of using technology the way it had been intended to.
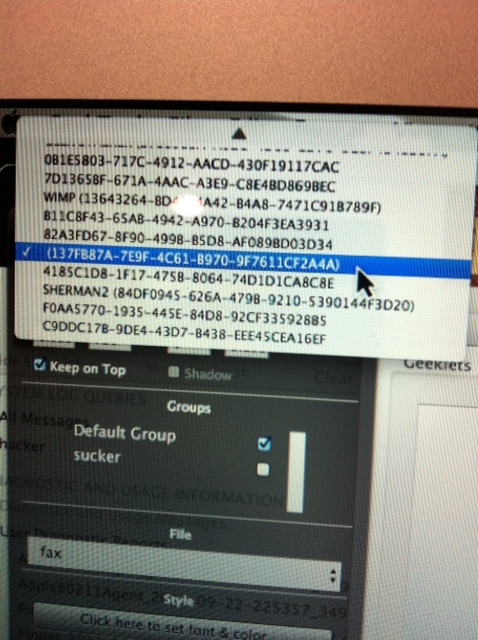
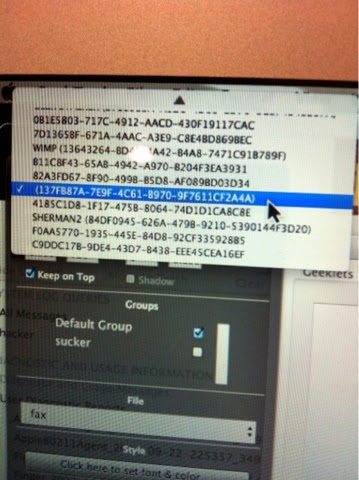
I knew when I tried to email Amanda at Apple the logs I had created and received the message 'password/UN rejected' for all 3 gmails I had built into the mail client, it only confirmed my suspicions I had been trying to ignore that 'Sherman' had some how managed to follow me to another state (I had lived in MD then moved to FL and was at a 4th address that he had relentlessly been stalking me.) Even tried to build in a 4th email thru the mail client which worked until I tried to mail the logs. I was completely blown away! I finally had what I thought would be proof of someone else on my laptop lurking behind the scenes. I had noticed an app that I thought had come with my MAC called the GeekTool App (pictures below) which I had tried to open previous to this just to check it out but had been unsuccessful but for whatever reason made it my mission to open it in hopes it could lead me to some answers. When I finally got it open, I saw 3 sequences of numerous numbers and letters already built in and assumed it was some how what was programming and had been compromised by 'Sherman'. After manipulating the sequences and checking boxes that weren't check and unchecking boxes that were checked it would some how disconnect the hacker from my laptop. I even added more sequences that were equivalent in length of made up numbers and letters in hopes to deter the hacker. (Geek Tool App below)
It had a box to name the sequences and I named one WIMP, SHERMAN, SHERMAN 1 etc. and before I knew it they started multiplying rapidly. I figured if I screwed something up that Apple would be able to walk me through how to fix it. Only to find out that this App had NOT been an Apple App and the Geek Squad where I had purchased the MAC (Best Buy) had not put this mysterious App on my laptop at all. It was a total mystery how it was even on my MacBook Air at all. All I know, by manipulating this App I came across some very strange things that were behind the scenes... For one the next picture will show two screens of ALL THE EMAILS that some how ended up on my MAC. You can see the ones I built in had labeled names of the actual gmail I had built so that I could tell them apart. By this time I had accumulated over 100 email addresses in hopes to get rid of the hacker thinking he was able to find me by my email addresses. I just kept creating new ones which wasn't an easy task keeping up with them all and as you can see there were multiple addresses added by the hacker because I certainly had not added them and as you can see were not labeled to the actual address used... But why? You would think someone could give me an answer but that never happened. In fact I'm sure many I spoke with doubted anything I had to say when it came to a 'hacker' hijacking my technology.
By this time I was thrilled that I was able to capture what my eyes were seeing this time around because ALL THE CRAZY I would get subjected on all the other computers would end up so corrupt, I would have no proof of anything. So I really got my hopes up when I reached another senior level at Apple by the name of Erin Elliason who took great interest that an Apple product had in fact been hacked and to a degree that no one could fathom. She was the one who promised to replace my MacBook Air if they were unable to resolve the 'Sherman' I was able to expose for my eyes only (which seemed more then odd that when I took my MAC to Apple for them to get some kind of diagnostic on it, Sherman, as a USER PROFILE with ADMIN RIGHTS could not be seen...) Only at my house but I knew from almost 2 years of torture by that time to take whatever pictures I could because it seemed Sherman always managed to undo anything I would get subjected to when I would take my computer or cell whenever it would act 'possessed' and make me come across as 'CRAZY'. Yep... Sure, UN HUH! It was really getting old trying to explain for example my LG ALLY which got replaced 3 times at one point was having a mind of it's own with the battery charger. It would show a full charge then ZAP no battery life, would plug it in, show a full charge again, unplug and ZAP no battery life but as soon as I took it to Verizon Wireless, not really thinking too much about it except it must be a defective battery and they'll replace it, but it worked fine in the store! They were nice enough to replace the battery but that was the beginning of the hacker toying with my mind in so many different ways that I have blocked out a lot today because it was never ending! Of course, waving my address up and down the screen when I lived by myself was definitely creepy! I do remember the times my cell would do something whacked (example: tried to type in an entry into LG about the hacker and every time I typed it, it backed spaced through every letter typed and delete it) by the time this occurred - I knew the hacker could hear me AND see me whether I was using my phone or not and had caught onto his game so to test my sanity I placed the phone in another room, went to my Step Mother and quietly told her to witness what the hacker was doing, which she did and voila! (I had taped over the camera lense by this time so he couldn't see - learned that the hard way to) she got to witness 'my world of crazy' then purposely said out loud 'watch when I type this entry, it's going to delete each one when I finish' and of course it didn't do it! I knew he could hear me!! He has set me up so often already to prove the actions of someone else on my cell to only look like a fool when it wouldn't do it... Time and time again. I caught onto to his sick, twisted game. When was it going to stop?
Sunday, March 11, 2012
My Stalking Cyber Hacker
Have had ALL my computers, cell phones, & printers viciously compromised ever since my Dell Laptop literally got hacked into right before my eyes around 2 years ago. I was so blind to the nightmare that I would be subjected to, all because I was in total disbelief to what I was witnessing when my hacker named 'Sherman' was 'hacking' his way into my computer & ended up taking total control of my laptop - ALL because I was too naive to believe 'this only happens to other people', NOT ME.
Tuesday, February 14, 2012
Cyber Hacker Attack whose name is Sherman
I have been stalked by a Hacker since March 2010 who has appeared as 'Sherman' twice & just recently on my Apple MacBook Air & took administrative rights both times. It's been almost 2 years since he 1st appeared & has been tormenting me by compromising every cell phone (numerous, in hopes to put it to a stop) and 7 computers, 4 printers. Not to mention 'phone trapped'..... Talk about BIZAARE. My story needs to be heard and put a stop to the never ending torment he has been subjecting me to. He belongs behind bars & I deserve peace of mind & freedom to use technology the way I was able to before my stalking hacker invaded my life & has made it a living hell in the 'Twilight Zone'. All I can say is - Thank you Apple, because of the iPad & iPhone, although the network connections have been compromised & odd things have occurred on all Apple Devices, the hacker has been unable to corrupt them to a degree of preventing me from getting my story out & I can once again, for the most part, enjoy using technology! FYI, my current location is far from where the map has me located in IN... I live in FL. That's funny, cuz my Facebook current location is usually Doylestown, PA... Weather App had me in Kansas for awhile and I have never been close to those areas. HMMMMMM, very interesting.
Labels:
bully,
compromised,
Computer,
Connection,
crime,
Cyber,
Cybercrime,
Cybercrime Unit,
Griefer,
hacked,
hacker,
high-tech,
illegal,
new technology,
phreaks,
stalked,
stalker,
Stalking,
technology,
Terror
Subscribe to:
Posts (Atom)