2-10-13 Tweet (Added some additional statements today toward the end 3-4-13) but had tweeted from my @StalkedByHacker Twitter account which continuously keeps getting suspended... Going on 8 times as of the other day) Have another account > @TheOnlyChristie ~~ Follow Me! ...
And now that I have to accept the fact that my hacker is on a twisted ego trip... Comes and goes. Just to make sure I don't forget him I guess - Whatever - He has relentlessly had a necessity to 'show off' all his black magic for so long, I don't even know (sometimes) if it's the hacker up to his old voodoo or IF it just MAY BE a fluke with technology! That's so deranged but I guess part of his strategy. I know earlier I got a pop up (which I have popups blocked but it is what it is) and ZoomPower requested I do a survey for my Twitter use. Real? Maybe. ALL the BOGUS sites my hacker would set me up to fall for hook, line and sinker just to set me up for 'Sherman's' voodoo to inflict more questions then answers on HOW, WHY, & WHO the hell?? I guess if I actually knew who the WHO was, would help answer the WHY? Maybe? Well my XHusband stalked me for years & all I know is me & my kids had to stay in hiding for our safety so when he dropped dead suddenly which was no surprise, just glad it was him & not us, but I thought I had found peace finally. He always did threaten me, If I can't have you, nobody can...can evil spirits become tech Savvy? He had said on a few occasions that he would fake his death then finish me off when I least expected it. The things I have witnessed & been subjected to seem UNREAL, as in 'That's not possible' to the mind of a logical person which I never had a problem facing whatever reality was thrown my way... But my hacker's goal was to try and drive me insane. The closest I got was to question my own sanity time & time again that I may just have to accept that this chapter of my life may not give me the closure I need and the answers to prevent this Twilight Zone existence from ever happening to anyone else. I was one to ALWAYS fix any 'wrong', 'evil' obstacles that came my way and thought justice would be served & SOME law agency would come to my rescue... not the case. And because the 'hacker' has gotten away with tormenting since 3/2010 & no one to turn to, although since accomplishing creating a Twitter account, the Hacking Griefer seems to have backed off compared to what he was doing but He has done that before, when I first moved from MD to FL to only appear a 2nd time as 'Sherman' as a profile who stole Admin Rights on my brand new Apple MacBook Air, just to prove a point that although not controlling my mouse anymore on my devices, including my cell, which he had done before I had an iphone, on my LG ALLY smartphone, he was still corrupting EVERYthing I owned technology wise... yes, printers too; 4 total & as far as I know, stalking me obviously. Having no one to turn to & constant fear of the all the CYBER terror he has gotten away with has literally affected me to such a degree, I am no longer the person I used to be before ALL this CYBER ABUSE (Stalking). It makes you feel so vulnerable to an unimaginable degree.
All I can do is put it in Gods hands AND believe that Good still does exist even if it comes down to not give in to believing otherwise. #StopCyberTerror. #LovePeaceUnity
Have had ALL my computers (7), printers (4) & numerous cell phones viciously compromised ever since my Dell literally got hacked into right before my eyes over 2 years ago. I was so blind to the nightmare that I would be subjected to, all because I was in total disbelief to what I was witnessing when my hacker named Sherman was hacking his way & ended up taking total control of my devices - ALL because I was too naive to believe this only happens to other people, NOT ME.
Monday, March 4, 2013
Friday, February 15, 2013
1st Twitter Follower - Threat by Hacker
2-15-13
Check out how 'Elisabeth' has 0 Followers, 0 Tweets & Following 0 people. After all the torment my hacker has put me through, of course, I'm thinking the Profile statement was a direct threat from my Hacker, Sherman, because he had turned everything into like a game to him by not letting me create a Twitter account. I just kept being persistent then one day for whatever reason, after over 6 months of trying, when it seemed I had actually succeeded, @StalkedByHacker, seemed more then appropriate to create as my UN. Of course I didn't have a clue how Twitter worked & it took quite awhile to get the hang of it. Seems, as if, I continue to learn something new about it every day. All I knew, I believe it was my my iPhone that I had succeeded to being able to create the account on after creating another one by a name I had come up with when a tech from Best Buy in MD had trouble & took several times before being able to set up my very 1st iPad for me since the hacker had made it impossible for me to do from my parents house or my house. I recall the Tech stating she had never come across such strange behavior from an iPad and she was one who had mentioned to me that I would probably have to change my identity, including social security #, since at that point it was very obvious my identity had been stolen, of course, having no clue the hacker would be so persistent in following to FL, to a 3rd then 4th new address I had moved to since the 1st location of the hacker intrusion.
All I knew, I was finally going to - hopefully - be able to vent to the world about my stalking hacker. It couldn't hurt & I knew it was a big 'IF'. Yes, Sherman, my hacker definitely made it almost impossible for me to type the 140 characters I had so anxiously had been waiting to do for quite awhile. In fact, he made it very difficult for awhile and I would just submit whatever I had managed to type from either my iPad or iPhone even WITH all the typos & some tweets looking Chinese but as time went on & ALL the porn and very odd people (the Hacker being plenty of the UNs I came across) I have pretty much have been more free to use technology then I've been able to since 3/2010! The only problem I keep coming across is my passwords continuously getting changed by Hacker where I have to reset it, mostly to my FB & Twitter but I am still going through BS with my MacBook Air that I still am unable to use & have been dealing with that since I bought it 9/2011.
May not be able to use a PC but after much persistence had my iPads & iPhones replaced each a few times but had also been promised by Apple to get my MacBook Air replaced which hasn't happened yet. But thank God for Apple. otherwise. If it hadn't been for Apple I would never had been able to get the proof that I have managed to do so & I believe Sherman is always going to be lurking & stalking me but NOW in hiding until he can find another opportunity to try and do one of his voodoo black magic Cyber terror pounces when he thinks I am least expecting it...
Pic of my 1st Follower with my account @StalkedByHacker that I've managed to hold onto miraculously... Read the profile > a taste of 'Sherman's' terror...
Check out how 'Elisabeth' has 0 Followers, 0 Tweets & Following 0 people. After all the torment my hacker has put me through, of course, I'm thinking the Profile statement was a direct threat from my Hacker, Sherman, because he had turned everything into like a game to him by not letting me create a Twitter account. I just kept being persistent then one day for whatever reason, after over 6 months of trying, when it seemed I had actually succeeded, @StalkedByHacker, seemed more then appropriate to create as my UN. Of course I didn't have a clue how Twitter worked & it took quite awhile to get the hang of it. Seems, as if, I continue to learn something new about it every day. All I knew, I believe it was my my iPhone that I had succeeded to being able to create the account on after creating another one by a name I had come up with when a tech from Best Buy in MD had trouble & took several times before being able to set up my very 1st iPad for me since the hacker had made it impossible for me to do from my parents house or my house. I recall the Tech stating she had never come across such strange behavior from an iPad and she was one who had mentioned to me that I would probably have to change my identity, including social security #, since at that point it was very obvious my identity had been stolen, of course, having no clue the hacker would be so persistent in following to FL, to a 3rd then 4th new address I had moved to since the 1st location of the hacker intrusion.
All I knew, I was finally going to - hopefully - be able to vent to the world about my stalking hacker. It couldn't hurt & I knew it was a big 'IF'. Yes, Sherman, my hacker definitely made it almost impossible for me to type the 140 characters I had so anxiously had been waiting to do for quite awhile. In fact, he made it very difficult for awhile and I would just submit whatever I had managed to type from either my iPad or iPhone even WITH all the typos & some tweets looking Chinese but as time went on & ALL the porn and very odd people (the Hacker being plenty of the UNs I came across) I have pretty much have been more free to use technology then I've been able to since 3/2010! The only problem I keep coming across is my passwords continuously getting changed by Hacker where I have to reset it, mostly to my FB & Twitter but I am still going through BS with my MacBook Air that I still am unable to use & have been dealing with that since I bought it 9/2011.
May not be able to use a PC but after much persistence had my iPads & iPhones replaced each a few times but had also been promised by Apple to get my MacBook Air replaced which hasn't happened yet. But thank God for Apple. otherwise. If it hadn't been for Apple I would never had been able to get the proof that I have managed to do so & I believe Sherman is always going to be lurking & stalking me but NOW in hiding until he can find another opportunity to try and do one of his voodoo black magic Cyber terror pounces when he thinks I am least expecting it...
Pic of my 1st Follower with my account @StalkedByHacker that I've managed to hold onto miraculously... Read the profile > a taste of 'Sherman's' terror...
Labels:
Apple,
bully,
Cyber,
Cyber Terror,
Dell,
Griefer,
hacked,
hacker,
MacBook Air,
stalker
Location:
Port St Lucie Port St Lucie
Wednesday, February 13, 2013
@StalkedByHacker Suspended the 6th time
Still believe Good Conquers evil. It's disturbing that vultures feast on the broken and weak but don't mistaken kindness for stupid. Look forward to the feast. Fuck off. God bless.
I came across the above quotation on my iPad and recall it being so much longer & was actually a response I had made (not what's above exactly) but much longer & descriptive. When I copied it to Blog about it on my iPad and opened the App up to paste it, of course, I got an error where I was unable to do so. Then it auto went to log into it as if I had never logged into it before to go to my blogspot. I had just finished transferring over info re: ALL the support tickets I have had to submit to Twitter because I just had to submit another one & wanted ALL info on my iPad & iPhone for reference to be the same. My twitter account @StalkedByHacker has been suspended 6 times which makes no sense. I understand the 1st time it happened because I had been Following to aggressively which once I read the VERY vague policies understood that's against their policies. But the next 5 times - I am clueless as to why. I do know that I have definitely experienced some very strange people which I guess is to be expected but will paste copies of the very interesting interactions I have had with Twitter world, the first Follower being an Elisabeth Aldo who had 0 Followers, 0 Following AND 0 tweets but the profile read "I will Fucken destroy you" period. A bit odd! Of course everything I have been subjected to with all of the Hacker's voodoo black magic tricks and since it took me at least 6 months to even be able to create an account because of continuing compromising by 'Sherman', of course I questioned if that was intended as a direct threat from my hacker or what. I got several odd Followers & obviously blocked them & it never failed when I did a search on a specific one, they no longer existed. I was always dissecting their profiles & taking note of the amount of tweets, followers & Following cuz it always seemed the account had just been created for whatever reason. But when you have been subjected to the HELL that the FBI, local police and Cybercrime unit are all aware of but have yet to help me crucify & bring justice to the 'network' that I believe has been behind ALL the crazy since Sherman 1st appeared on my Dell laptop in 4/2010 & remotely accessed me on EVERY cell & PC before I made the move from MD (where it occurred) to FL. Now when I say remote accessing, I am telling you SOMEONE was controlling what I could and could not to on my devices & controlled my mouse etc. believe me when I say this, YOU KNOW WHEN YOU HAVE NO CONTROL over a device using technology. Sherman made it a point to even go to the extreme of remote accessing & controlling my mouse at 2 different libraries that were an hour away from each other AND somehow knew to be waiting for me at my parents house when I logged into their PC & logged into their Verizon account on line so I could JUST accomplish what the police in MD told me I needed to do by reporting my hacker to www.ic3.gov, which he had managed to prevent that from happening on a brand new laptop I bought after the Sherman appearance on my Dell, 2 different libraries then at my parents house. It was beyond logical. Reality as it had once existed for me before the hacker is anything but REAL but those are the facts. I finally succeeded when I drove another hour farther from my parents to my son's house & his wife did it for me on her iPad. That's how I got introduced to Apple . From the time the police said that was my only option in April 2010, it wasn't until July 5, 2010 that my daughter-in-law succeeded to submitting what I thought was a crime of being stalked & someone intentionally making no secret that I no longer had the freedom to use technology that everyone just takes for granted. It didn't do any good except the 4th LG android that got replaced was no longer being remotely accessed shortly before my move to FL. New cell, another brand new PC and I made the mistake to think I was in the free & clear of ALL the torment that was nonstop up to the point of getting the FBI involved. But the Griefer at that point had decided to stay in cognito until the whopping CYBERterror that blindsided me again. The weird part is, I never really thought he just went away. I had a hunch that he was still lurking just waiting for the right time to prove to me I was powerless over a coward who stays in hiding physically who obviously is a very sick individual but kept telling myself I was being paranoid. Yep, strange things kept happening, kept buying new PCs, cells, printers because of corruption that continued to possess my technology. But as for twitter, time before last, I was unable to submit a support ticket on my iPad because of what I call Hacker BOGUS errors that I have grown so accustomed to but will never get over the fact that after 'Sherman' appeared a 2nd time on my most recent purchase - Apple MacBook Air that the FBI claims it must be someone I know & since no money has been stolen it should be up to the police, who I have gone to on 7 or 8 different occasions to only tell me they don't have the resources to stop this evil network from their despicable intrusive actions.
Back to Twitter... I had to have my sister submit to Twitter support. Last time, from all devices (I think it was the famous fictitious websites the hacker enjoys toying with me with) I could never receive a reply like the previous times with 3 different emails I included for them to respond to that I had used previously so finally used entirely new one that FINALLY got the reply notification & I was up and running again. This time same compromising - I was unable to input my UN @StalkedByHacker & in the phone number box I literally put 'what's the point' followed by my phone number and figured what the hell, might as well use the StalkedByHacker email I used previously and it actually submitted. No user name, phone number NOT, BUT received an acknowledgement reply to an entirely different email then what I gave them. Odd? Paranoid? It just doesn't make any sense. I have fallen prey to so many fictitious emails & websites that totally screwed me & don't know what to do. I have almost 7,000 followers, which is another odd thing, my account is 'suspended', can't use it, can't even pull it up through my other account @TheOnlyChristie; it just just says 'no such account' so how am I receiving email notifications of continuing Followers during this whole time as recent as an hour ago? This is where I can hope to get through to people the 'CRAZY' that I have lived going on 3 years now. Please ALWAYS shutdown, AFTER disabling Internet connection and unplug anything to the modem/router. As for the first quote above? I am more thorough to have written something so deep without giving it a proper title or where I used it at and WHY was it opened to such a confound statement just waiting for me to read?
I am tired. Hopefully tomorrow in a separate blog I can share the Elisabeth Profile that I believe is a direct threat intended to me by my hacker and the more then interesting ones that they claim they know who my hacker is...
God Bless. Peace Out.
I came across the above quotation on my iPad and recall it being so much longer & was actually a response I had made (not what's above exactly) but much longer & descriptive. When I copied it to Blog about it on my iPad and opened the App up to paste it, of course, I got an error where I was unable to do so. Then it auto went to log into it as if I had never logged into it before to go to my blogspot. I had just finished transferring over info re: ALL the support tickets I have had to submit to Twitter because I just had to submit another one & wanted ALL info on my iPad & iPhone for reference to be the same. My twitter account @StalkedByHacker has been suspended 6 times which makes no sense. I understand the 1st time it happened because I had been Following to aggressively which once I read the VERY vague policies understood that's against their policies. But the next 5 times - I am clueless as to why. I do know that I have definitely experienced some very strange people which I guess is to be expected but will paste copies of the very interesting interactions I have had with Twitter world, the first Follower being an Elisabeth Aldo who had 0 Followers, 0 Following AND 0 tweets but the profile read "I will Fucken destroy you" period. A bit odd! Of course everything I have been subjected to with all of the Hacker's voodoo black magic tricks and since it took me at least 6 months to even be able to create an account because of continuing compromising by 'Sherman', of course I questioned if that was intended as a direct threat from my hacker or what. I got several odd Followers & obviously blocked them & it never failed when I did a search on a specific one, they no longer existed. I was always dissecting their profiles & taking note of the amount of tweets, followers & Following cuz it always seemed the account had just been created for whatever reason. But when you have been subjected to the HELL that the FBI, local police and Cybercrime unit are all aware of but have yet to help me crucify & bring justice to the 'network' that I believe has been behind ALL the crazy since Sherman 1st appeared on my Dell laptop in 4/2010 & remotely accessed me on EVERY cell & PC before I made the move from MD (where it occurred) to FL. Now when I say remote accessing, I am telling you SOMEONE was controlling what I could and could not to on my devices & controlled my mouse etc. believe me when I say this, YOU KNOW WHEN YOU HAVE NO CONTROL over a device using technology. Sherman made it a point to even go to the extreme of remote accessing & controlling my mouse at 2 different libraries that were an hour away from each other AND somehow knew to be waiting for me at my parents house when I logged into their PC & logged into their Verizon account on line so I could JUST accomplish what the police in MD told me I needed to do by reporting my hacker to www.ic3.gov, which he had managed to prevent that from happening on a brand new laptop I bought after the Sherman appearance on my Dell, 2 different libraries then at my parents house. It was beyond logical. Reality as it had once existed for me before the hacker is anything but REAL but those are the facts. I finally succeeded when I drove another hour farther from my parents to my son's house & his wife did it for me on her iPad. That's how I got introduced to Apple . From the time the police said that was my only option in April 2010, it wasn't until July 5, 2010 that my daughter-in-law succeeded to submitting what I thought was a crime of being stalked & someone intentionally making no secret that I no longer had the freedom to use technology that everyone just takes for granted. It didn't do any good except the 4th LG android that got replaced was no longer being remotely accessed shortly before my move to FL. New cell, another brand new PC and I made the mistake to think I was in the free & clear of ALL the torment that was nonstop up to the point of getting the FBI involved. But the Griefer at that point had decided to stay in cognito until the whopping CYBERterror that blindsided me again. The weird part is, I never really thought he just went away. I had a hunch that he was still lurking just waiting for the right time to prove to me I was powerless over a coward who stays in hiding physically who obviously is a very sick individual but kept telling myself I was being paranoid. Yep, strange things kept happening, kept buying new PCs, cells, printers because of corruption that continued to possess my technology. But as for twitter, time before last, I was unable to submit a support ticket on my iPad because of what I call Hacker BOGUS errors that I have grown so accustomed to but will never get over the fact that after 'Sherman' appeared a 2nd time on my most recent purchase - Apple MacBook Air that the FBI claims it must be someone I know & since no money has been stolen it should be up to the police, who I have gone to on 7 or 8 different occasions to only tell me they don't have the resources to stop this evil network from their despicable intrusive actions.
Back to Twitter... I had to have my sister submit to Twitter support. Last time, from all devices (I think it was the famous fictitious websites the hacker enjoys toying with me with) I could never receive a reply like the previous times with 3 different emails I included for them to respond to that I had used previously so finally used entirely new one that FINALLY got the reply notification & I was up and running again. This time same compromising - I was unable to input my UN @StalkedByHacker & in the phone number box I literally put 'what's the point' followed by my phone number and figured what the hell, might as well use the StalkedByHacker email I used previously and it actually submitted. No user name, phone number NOT, BUT received an acknowledgement reply to an entirely different email then what I gave them. Odd? Paranoid? It just doesn't make any sense. I have fallen prey to so many fictitious emails & websites that totally screwed me & don't know what to do. I have almost 7,000 followers, which is another odd thing, my account is 'suspended', can't use it, can't even pull it up through my other account @TheOnlyChristie; it just just says 'no such account' so how am I receiving email notifications of continuing Followers during this whole time as recent as an hour ago? This is where I can hope to get through to people the 'CRAZY' that I have lived going on 3 years now. Please ALWAYS shutdown, AFTER disabling Internet connection and unplug anything to the modem/router. As for the first quote above? I am more thorough to have written something so deep without giving it a proper title or where I used it at and WHY was it opened to such a confound statement just waiting for me to read?
I am tired. Hopefully tomorrow in a separate blog I can share the Elisabeth Profile that I believe is a direct threat intended to me by my hacker and the more then interesting ones that they claim they know who my hacker is...
God Bless. Peace Out.
Labels:
Apple,
Cyber,
Cyber Terror,
Dell,
hacker,
MacBook Air,
Sherman,
stalker
Location:
Port St Lucie Port St Lucie
Sunday, January 27, 2013
Stalked By A Hacker
1-26-13
Honestly, ALL the advice I have been given by those who REALLY did understand the extent of what was happening, didn't work. I can't wrap my head around the 'logic' when it's anything but 'logical', what I believe is a network of people, (FBI thinks it's someone I know - so that makes it okay?) but although the extent of the insanity seems more personable, I think it's a much bigger picture and I have my theory that is so out there, but have had since April of 2010 to make reason out of nothing but 'CRAZY' and someone's obsession to play me like a "virtual" game piece of continuous CYBER bullying, which I will keep to myself until I hopefully am able to finish a book. WHY? WHO? If I knew the 'WHO' it would shed a whole lot of light but the FBI isn't willing to help me solve... WHY? Why would every law enforcement that we pay our tax money to, to protect us, too eager to close my case AFTER 'Sherman' appeared on my Apple MacBook Air 1 1/2 years after his 1st appearance on the Dell that seemed to have wiped out ALL it's identification that I had used NUMEROUS times when calling into Tech Support; 'Sherman' appears and my Dell no longer exists? How would 'Sherman' know to be waiting for me at my parent's house or for that matter at 2 different libraries that were about 50 miles away from each other? WHY ME? Which is what I should name my book... "StalkedByHacker WHY ME?" Why did it take me over 4 months to be able to create a Twitter account that has been suspended 5 X's, most recently last night WHILE I was in the middle of tweeting to over 6500 people about being remotely accessed at the 1st library? This time my support ticket isn't being acknowledged at all. Last time I had to have my sister submit the ticket because 'Sherman' prevented me from being able to submit a Support ticket from my iPad. I have ALOT of WHYs! I don't think anyone really wants the answers to. Reality? My Reality has been far from REAL ever since I noticed someone was toying with my Dell laptop that was obviously "possessed" and I still have to this day. It has never been turned on since I took flight to my parent's house in fear for my life because after being on my home LAN line for HOURS giving me the the total run around from the carrier I had at that time because I noticed I was connected to a public network etc. BOTH my LAN line and cell phone had no service when I woke up, and fled to the police station trying to explain hysterically that 'Sherman' was on my Dell laptop and had no service through VW w/ my cell (that was also 'possessed') OR my LAN line that was provided by Comcast and when I had fallen asleep, all I remember was watching my laptop erase pixel by pixel after technical support had 'helped' me... Didn't go over too well acting hysterical but their resolution was to go to www.ic3.gov and report the hacker to get ANY help and almost 3 years later. I guess ALOT of big "HOWs"? Come into play. So many insane, almost delusional events have happened ever since. Plenty happened previous... ALL on line with my DELL, LAN line AND cell. HOW? Was a hacker(?) able to remote access my LG ALLY Smartphone (I had replaced it w/ the old 'possessed' one I watched, literally, the analog clock on the front change to digital and my Text messaging had totally changed formats on me, which I found weird but not per say 'crazy' just thought it odd and when I called VW support regarding it I was told "Someone HAD to have replaced the SIMS card that was in it to have had made such drastic changes" which was absolutely ludicrous. But you get whatever knowledge Support has to offer, in hopes to 'reground' your thoughts of "I must be going crazy" but the best resolution and seemed I guess logical to whoever I spoke with, whether it was Technical or Customer support that whatever 'event' I had just experienced, whether it was my computer or cell is "That's not possible", pretty much casting my own insecurity of questioning my sanity. Be told that enough times by different people who are the "KNOW IT ALLS" and you start questioning your "Reality" - FACTS that you find no logic but yet was REAL and questionable sanity becomes your reality. BUT then God ALWAYS has a way a having the right person you cross paths with that give a FULL BLOWN REASON and explanation to their best ability that helps you find your footing AGAIN. Time and time again. Some more HOWs, if you have the answer by all means 'share' because I have more WHYs? And HOWs to twisted events that no one should have to endure without getting a resolution to resolve the BIG MYSTERY. After the police (after my 1st of numerous approaches to law enforcement) instructed me to report the initial crime to www.ic3gov, HOW was 'Sherman' able to remotely access my LG ALLY smartphone and control every aspect of what I could do and couldn't do? Was free the 1st, about 20 days I owned it, but 'Sherman' was able to LOCK me out from my pattern code I needed to do to use my phone and ALWAYS after store closing hours, then would magically work by the time VW would open. HOW was he able to literally control anything I tried to submit to support for help and turn Chinese? HOW was he able to compromise my cell some how, some way ex: zapping battery life even when plugged in BUT NEVER happen when I took it into VW... He was setting me up to seem "CRAZY" although I had learned after the police station incident, nothing gets resolved when you act IRRATIONAL no matter how FUCKEN IRRATIONAL the situation is. A true test of my sanity. HOW was he, no matter how many times I erased & restored to default, change my phone numbers (that was everyone's favorite resolution to fixing my COMPUTERS, LG ALLY CELL, IPADS, IPHONES etc.) which all it did was erase ANY proof that possibly could have been helpful and did not deter 'Sherman' especially w/ my 1st smartphone. I had it replaced, after changing the numbers too many times to keep count, my VW account was screwed up and after replacing my cell 2 times already, and someone controlling it, I forget what whacked out thing it was doing but ironically I was sent to a Retailer VW (since VW was sick and tired of me w/ my what even seemed to me, UNREAL stories) where for the 1st time it actually did whatever 'Sherman' normally would do to have it back to 'normal' mode (Coincidence? Or being in a brand new VW - RETAILER store have anything to do with Sherman Not being able to continue his charade?) Also - I had long since started taping paper over the camera lense cuz it seemed he could see me and when others were around. Started taking the batter out of it at night so he would stop invading my privacy and would send me bogus articles or have you tube waiting for me to open up, which I NEVER did! Plus for the 1st time I was able to show how it continuously gave me BOGUS errors of not letting me access websites like I was previous to making the mistake of inputting one of the 1st email addresses, that had very important info, that was confiscated when my Dell got hacked ex: My Benefits Resource page or any emails on the web etc. So anyway they were more then happy to replace my cell a 3rd or 4th time at this point but only after they WIPED out my VW account I had had ever since I owned a cell and make a brand new account with a FICTITIOUS name, in case 'Sherman' happened to have some sort of inside resource he had access to, AND change my number to a FL exchange even though I lived in MD at the time. That should, you would think, have taken care of it, at least with my cell. I failed to mention the numerous attempts I had made with my cell to report the hacker to www.ic3.gov since I had not been able to w/ a brand new laptop 'Sherman' took a snapshot of, even having a brand new modem/router I had replaced, too, at home, 2 libraries and my parent's house - all failed attempts because SHERMAN took control of the mouse. Except w/ my ALLY I was finally able to populate www.ic3.gov, input the HELL I had been subjected to, but was NEVER able to submit, just kept populating what I call BOGUS errors that I got way too familiar with these past (almost) 3 years. I was finally able to 7/5/10, 3 months after SHERMAN appeared & the police had instructed me to. My daughter in law who lived about 1 1/2 away from me used her iPad and submitted my story for me, my 2nd attempt of SOMEONE TO PUT A STOP TO ALL THE CRAZY UGLY that at that point, since has been my what seems 'delusional' reality that I could not escape from. All I know is the 3rd or 4th ALLY replacement seemed to do work. No more remote accessing, I had the 1st Brand new laptop replaced, although that was a battle in itself. I had only used it a couple days more after getting THAT new modem/router replaced since, I'm assuming, SHERMAN some how compromised it also. After using the brand new laptop about, 15 minutes of using it, it was like a big FLASH went off. I believe I had McAfee at the time (not that ANY antivirus helped) but it clearly said there had been 2 unsuccessful entries made but the 3rd one WAS successful and that was when the modem/router stopped working altogether. Again, Coincidence? Had the address out of NJ somewhere. When I attempted to print out the details of the report, my printer stopped working. Couldn't save it to a CD because that was one of the many things 'Sherman' corrupted, purposely so I would not be able to establish any evidence. Of course, this is all hindsight. Looking back there's so much more that makes sense now. It all seems so unreal trying to remember everything, but want people to know the seriousness and invasion that has taken place ever since I 1st noticed in February or March of 2010 that my Dell was acting 'possessed' and I was too naive to ever imagine my world would completely change. I moved to FL with another brand new Lenovo laptop, printer, and I thought, an LG ALLY cell that I had escaped the wrath of 'Sherman' from. There's more to the story, obviously is meant for a book with more detail. I was just hoping for a happy ending. I guess there are just too many HOWs? but most of all WHO? And WHY? Usually money's the root of evil... so. I do believe the phone trapping needs to be taken more seriously that I definitely fell pray to. I also believe having a LAN line ties into what I think is a huge elaborate scam that too many people have fallen victim to and don't even realize it. If you have any type of 24/7 tech support or anything that you are paying an amount that seems reasonable... Thinking, thinking, thinking the 3 addresses where 'Sherman' made his presence apparent where numerous cells, printers and computers were compromised ALL HAD LAN LINES AND INTERNET. How many victims are phone trapped today and of course don't know it, but more seriously, WHO? I don't have the answers, I wish I did. But what's most disturbing to me law enforcement agencies need to get it together and stop passing the buck off to another. WHY? Did 'Sherman' make it a point, although, I have my suspicions that privacy no longer exists in our world with technology, but WHY didn't 'Sherman' just stay in hiding like most hackers do? I am a witness to the extreme of how technology is being used when in the hands of EVIL but for whatever reason, wanted me to be quite aware that I was being stalked by a hacker! The few pics are from others on Twitter re: 'my' hacker... & I'm assuming the last one was a message intended for me from 'Sherman' in disguise as Elisabeth, when I was finally able to create my Twitter account, which I will put in separate blog also.
Honestly, ALL the advice I have been given by those who REALLY did understand the extent of what was happening, didn't work. I can't wrap my head around the 'logic' when it's anything but 'logical', what I believe is a network of people, (FBI thinks it's someone I know - so that makes it okay?) but although the extent of the insanity seems more personable, I think it's a much bigger picture and I have my theory that is so out there, but have had since April of 2010 to make reason out of nothing but 'CRAZY' and someone's obsession to play me like a "virtual" game piece of continuous CYBER bullying, which I will keep to myself until I hopefully am able to finish a book. WHY? WHO? If I knew the 'WHO' it would shed a whole lot of light but the FBI isn't willing to help me solve... WHY? Why would every law enforcement that we pay our tax money to, to protect us, too eager to close my case AFTER 'Sherman' appeared on my Apple MacBook Air 1 1/2 years after his 1st appearance on the Dell that seemed to have wiped out ALL it's identification that I had used NUMEROUS times when calling into Tech Support; 'Sherman' appears and my Dell no longer exists? How would 'Sherman' know to be waiting for me at my parent's house or for that matter at 2 different libraries that were about 50 miles away from each other? WHY ME? Which is what I should name my book... "StalkedByHacker WHY ME?" Why did it take me over 4 months to be able to create a Twitter account that has been suspended 5 X's, most recently last night WHILE I was in the middle of tweeting to over 6500 people about being remotely accessed at the 1st library? This time my support ticket isn't being acknowledged at all. Last time I had to have my sister submit the ticket because 'Sherman' prevented me from being able to submit a Support ticket from my iPad. I have ALOT of WHYs! I don't think anyone really wants the answers to. Reality? My Reality has been far from REAL ever since I noticed someone was toying with my Dell laptop that was obviously "possessed" and I still have to this day. It has never been turned on since I took flight to my parent's house in fear for my life because after being on my home LAN line for HOURS giving me the the total run around from the carrier I had at that time because I noticed I was connected to a public network etc. BOTH my LAN line and cell phone had no service when I woke up, and fled to the police station trying to explain hysterically that 'Sherman' was on my Dell laptop and had no service through VW w/ my cell (that was also 'possessed') OR my LAN line that was provided by Comcast and when I had fallen asleep, all I remember was watching my laptop erase pixel by pixel after technical support had 'helped' me... Didn't go over too well acting hysterical but their resolution was to go to www.ic3.gov and report the hacker to get ANY help and almost 3 years later. I guess ALOT of big "HOWs"? Come into play. So many insane, almost delusional events have happened ever since. Plenty happened previous... ALL on line with my DELL, LAN line AND cell. HOW? Was a hacker(?) able to remote access my LG ALLY Smartphone (I had replaced it w/ the old 'possessed' one I watched, literally, the analog clock on the front change to digital and my Text messaging had totally changed formats on me, which I found weird but not per say 'crazy' just thought it odd and when I called VW support regarding it I was told "Someone HAD to have replaced the SIMS card that was in it to have had made such drastic changes" which was absolutely ludicrous. But you get whatever knowledge Support has to offer, in hopes to 'reground' your thoughts of "I must be going crazy" but the best resolution and seemed I guess logical to whoever I spoke with, whether it was Technical or Customer support that whatever 'event' I had just experienced, whether it was my computer or cell is "That's not possible", pretty much casting my own insecurity of questioning my sanity. Be told that enough times by different people who are the "KNOW IT ALLS" and you start questioning your "Reality" - FACTS that you find no logic but yet was REAL and questionable sanity becomes your reality. BUT then God ALWAYS has a way a having the right person you cross paths with that give a FULL BLOWN REASON and explanation to their best ability that helps you find your footing AGAIN. Time and time again. Some more HOWs, if you have the answer by all means 'share' because I have more WHYs? And HOWs to twisted events that no one should have to endure without getting a resolution to resolve the BIG MYSTERY. After the police (after my 1st of numerous approaches to law enforcement) instructed me to report the initial crime to www.ic3gov, HOW was 'Sherman' able to remotely access my LG ALLY smartphone and control every aspect of what I could do and couldn't do? Was free the 1st, about 20 days I owned it, but 'Sherman' was able to LOCK me out from my pattern code I needed to do to use my phone and ALWAYS after store closing hours, then would magically work by the time VW would open. HOW was he able to literally control anything I tried to submit to support for help and turn Chinese? HOW was he able to compromise my cell some how, some way ex: zapping battery life even when plugged in BUT NEVER happen when I took it into VW... He was setting me up to seem "CRAZY" although I had learned after the police station incident, nothing gets resolved when you act IRRATIONAL no matter how FUCKEN IRRATIONAL the situation is. A true test of my sanity. HOW was he, no matter how many times I erased & restored to default, change my phone numbers (that was everyone's favorite resolution to fixing my COMPUTERS, LG ALLY CELL, IPADS, IPHONES etc.) which all it did was erase ANY proof that possibly could have been helpful and did not deter 'Sherman' especially w/ my 1st smartphone. I had it replaced, after changing the numbers too many times to keep count, my VW account was screwed up and after replacing my cell 2 times already, and someone controlling it, I forget what whacked out thing it was doing but ironically I was sent to a Retailer VW (since VW was sick and tired of me w/ my what even seemed to me, UNREAL stories) where for the 1st time it actually did whatever 'Sherman' normally would do to have it back to 'normal' mode (Coincidence? Or being in a brand new VW - RETAILER store have anything to do with Sherman Not being able to continue his charade?) Also - I had long since started taping paper over the camera lense cuz it seemed he could see me and when others were around. Started taking the batter out of it at night so he would stop invading my privacy and would send me bogus articles or have you tube waiting for me to open up, which I NEVER did! Plus for the 1st time I was able to show how it continuously gave me BOGUS errors of not letting me access websites like I was previous to making the mistake of inputting one of the 1st email addresses, that had very important info, that was confiscated when my Dell got hacked ex: My Benefits Resource page or any emails on the web etc. So anyway they were more then happy to replace my cell a 3rd or 4th time at this point but only after they WIPED out my VW account I had had ever since I owned a cell and make a brand new account with a FICTITIOUS name, in case 'Sherman' happened to have some sort of inside resource he had access to, AND change my number to a FL exchange even though I lived in MD at the time. That should, you would think, have taken care of it, at least with my cell. I failed to mention the numerous attempts I had made with my cell to report the hacker to www.ic3.gov since I had not been able to w/ a brand new laptop 'Sherman' took a snapshot of, even having a brand new modem/router I had replaced, too, at home, 2 libraries and my parent's house - all failed attempts because SHERMAN took control of the mouse. Except w/ my ALLY I was finally able to populate www.ic3.gov, input the HELL I had been subjected to, but was NEVER able to submit, just kept populating what I call BOGUS errors that I got way too familiar with these past (almost) 3 years. I was finally able to 7/5/10, 3 months after SHERMAN appeared & the police had instructed me to. My daughter in law who lived about 1 1/2 away from me used her iPad and submitted my story for me, my 2nd attempt of SOMEONE TO PUT A STOP TO ALL THE CRAZY UGLY that at that point, since has been my what seems 'delusional' reality that I could not escape from. All I know is the 3rd or 4th ALLY replacement seemed to do work. No more remote accessing, I had the 1st Brand new laptop replaced, although that was a battle in itself. I had only used it a couple days more after getting THAT new modem/router replaced since, I'm assuming, SHERMAN some how compromised it also. After using the brand new laptop about, 15 minutes of using it, it was like a big FLASH went off. I believe I had McAfee at the time (not that ANY antivirus helped) but it clearly said there had been 2 unsuccessful entries made but the 3rd one WAS successful and that was when the modem/router stopped working altogether. Again, Coincidence? Had the address out of NJ somewhere. When I attempted to print out the details of the report, my printer stopped working. Couldn't save it to a CD because that was one of the many things 'Sherman' corrupted, purposely so I would not be able to establish any evidence. Of course, this is all hindsight. Looking back there's so much more that makes sense now. It all seems so unreal trying to remember everything, but want people to know the seriousness and invasion that has taken place ever since I 1st noticed in February or March of 2010 that my Dell was acting 'possessed' and I was too naive to ever imagine my world would completely change. I moved to FL with another brand new Lenovo laptop, printer, and I thought, an LG ALLY cell that I had escaped the wrath of 'Sherman' from. There's more to the story, obviously is meant for a book with more detail. I was just hoping for a happy ending. I guess there are just too many HOWs? but most of all WHO? And WHY? Usually money's the root of evil... so. I do believe the phone trapping needs to be taken more seriously that I definitely fell pray to. I also believe having a LAN line ties into what I think is a huge elaborate scam that too many people have fallen victim to and don't even realize it. If you have any type of 24/7 tech support or anything that you are paying an amount that seems reasonable... Thinking, thinking, thinking the 3 addresses where 'Sherman' made his presence apparent where numerous cells, printers and computers were compromised ALL HAD LAN LINES AND INTERNET. How many victims are phone trapped today and of course don't know it, but more seriously, WHO? I don't have the answers, I wish I did. But what's most disturbing to me law enforcement agencies need to get it together and stop passing the buck off to another. WHY? Did 'Sherman' make it a point, although, I have my suspicions that privacy no longer exists in our world with technology, but WHY didn't 'Sherman' just stay in hiding like most hackers do? I am a witness to the extreme of how technology is being used when in the hands of EVIL but for whatever reason, wanted me to be quite aware that I was being stalked by a hacker! The few pics are from others on Twitter re: 'my' hacker... & I'm assuming the last one was a message intended for me from 'Sherman' in disguise as Elisabeth, when I was finally able to create my Twitter account, which I will put in separate blog also.
Friday, September 7, 2012
Twitter Account Suspended... Hacker?
9-7-12 >>> I am so confused about the twitter account that had taken me more then 6 months to set up. Every time I tried to create it, just like everything else I attempted to do with any device with technology, it got compromised some how, some way. I made numerous attempts, gave up, would wait awhile, try again, of course unsuccessfully, but I KNEW what I was up against. Then for some odd reason, after attempting on and off for over 6 months - I DID IT - I think. I knew nothing about how Twitter worked except I heard about daily from various news sources and it seemed intriguing, but I knew better then to get my hopes up... Why is my stalking hacker allowing me to create a twitter account now? Haven't been able to google search on how to use Twitter but let me give it a shot... I actually succeeded and when I got to the point of entering a User Name, which I hadn't really thought about cuz I had never gotten that far in creating one, but when asked, I didn't hesitate to create @StalkedByHacker & felt victorious to have been able to do that... I was so conflicted - this was probably another 'set me up' by my stalking hacker, who toyed with my sanity for over 2 years.
Seriously, take a moment and really think the next time you attempt to do anything on your computer and it being impossible to succeed whatever it was you were attempting to do... Google search something, create an email account, retrieve your emails, send an email out, try to open up a specific website, change a password, log into a website that does open up, but need to use a UN & password you have just used recently... I could go on and on - let's keep it basic. You are habit of creature and log into your FB account daily to 'share'... You have used the same UN & password for awhile & you go through the motions to get - we'll go with UN and/password incorrect... okay, no biggie, must have a typo somewhere. Try it again. Same error. Really? I know I typed it in right this time but let's do it again... But slower just to make sure I successfully log in, thinking how bad you want to share the most precious picture of an animal you love, maybe that special moment of capturing a precious pic of your child's very first day of kindergarten - or maybe that joyous victory of the child who is all grown up & just graduated from high school ready to go out into the world... Huh? This time a different error - hmmmm. Okay, no big deal. Something's obviously wrong with the site. Will have my 'sharing' moment tomorrow as soon as I get a good night sleep and have my cup of coffee. Happens all the time - right? Must be a 'fluke'. Then you realize that you promised a family member that you were going to email them that recipe you had been promising them forever, so you figure, okay, let me at least get that done before I call it a night. You reopen the email you had already logged into earlier, but for some reason it kicked you out... Log in with the familiar UN & password & some pop up window blocks you from being able to even input your password... Frustrated? Nope, just wish this computer wasn't 'acting' up. And figure, you know what? - I'll just pull up the recipe that I had put in my recipe folder and print it out since I am going to see them tomorrow anyway... No big deal... Really? Can't find the Recipe folder you just went into before you tried to email it to make sure you had the right recipe and NOW you can't find the darn Recipe folder. Okay, let's call it a night. I must be more tired then I thought. I'll just print it out real quick in the morning... The next morning while having your cup of coffee, you decide to print out that recipe... AHA! I knew it, must have been tired, the Recipe Folder was right where I always have it. Send to the printer... Okay now the printer's doesn't want to work! Whatever!! I'll get to it when I get home. So weird, huh? Nope. Weird, odd, disturbing & "coincidences" becomes your way of dealing with a very twisted hacker that gains pleasure of doing this to naive, innocent people all the time. But think about dealing with the above frustrated scenario, day in and day out for over 2 years!! I almost have my sanity back (I think) since my Hacking Griefer seems to have moved on...mmm Stalking? Thru my cell still? Probably then again, maybe not. What's the twisted little phreak gonna do? Don't give a shit. More like (hopefully) he's moved on... Right in front of the big ass truck going 80mph. All I can say is at least now I have a great excuse whenever there is a 'real' fluke while I have my freedom back with technology ... "The Hacker did it" & guess what? I don't give a damn!! Ha! Whatever!! IIWII - Moving Forward. Enjoying technology the way I have been trying to since way before I moved from MD, when 'Sherman' was on the prowl just waiting for just the right person to target... Who's next? I wonder how often the 'twilight zone' I encountered, has been reported by others? I seriously hope the hacker isn't attempting at this moment to make someone else questioning their sanity... I think being able to reverse IP's & zoom in on a hacker's location just might have something to do with my new found freedom. I love Apple!! But what I really want to know is... Why the hell did my Twitter account get suspended? >>>> guess I'll never know when I contacted @support they never really explained why, just that they were sorry & I had to guarantee that I had, in fact, read ALL their rules... Yea... Unhuh - RIGHT!!! My Twitter was out of commission for about 2 full days. I'm up and running again now & think I have around 1,500 Followers... So exciting!!! I was so fricken clueless, but I'm getting there. Follow me on Twitter @StalkedByHacker! And tweet me. Let's ROLL : )))
Seriously, take a moment and really think the next time you attempt to do anything on your computer and it being impossible to succeed whatever it was you were attempting to do... Google search something, create an email account, retrieve your emails, send an email out, try to open up a specific website, change a password, log into a website that does open up, but need to use a UN & password you have just used recently... I could go on and on - let's keep it basic. You are habit of creature and log into your FB account daily to 'share'... You have used the same UN & password for awhile & you go through the motions to get - we'll go with UN and/password incorrect... okay, no biggie, must have a typo somewhere. Try it again. Same error. Really? I know I typed it in right this time but let's do it again... But slower just to make sure I successfully log in, thinking how bad you want to share the most precious picture of an animal you love, maybe that special moment of capturing a precious pic of your child's very first day of kindergarten - or maybe that joyous victory of the child who is all grown up & just graduated from high school ready to go out into the world... Huh? This time a different error - hmmmm. Okay, no big deal. Something's obviously wrong with the site. Will have my 'sharing' moment tomorrow as soon as I get a good night sleep and have my cup of coffee. Happens all the time - right? Must be a 'fluke'. Then you realize that you promised a family member that you were going to email them that recipe you had been promising them forever, so you figure, okay, let me at least get that done before I call it a night. You reopen the email you had already logged into earlier, but for some reason it kicked you out... Log in with the familiar UN & password & some pop up window blocks you from being able to even input your password... Frustrated? Nope, just wish this computer wasn't 'acting' up. And figure, you know what? - I'll just pull up the recipe that I had put in my recipe folder and print it out since I am going to see them tomorrow anyway... No big deal... Really? Can't find the Recipe folder you just went into before you tried to email it to make sure you had the right recipe and NOW you can't find the darn Recipe folder. Okay, let's call it a night. I must be more tired then I thought. I'll just print it out real quick in the morning... The next morning while having your cup of coffee, you decide to print out that recipe... AHA! I knew it, must have been tired, the Recipe Folder was right where I always have it. Send to the printer... Okay now the printer's doesn't want to work! Whatever!! I'll get to it when I get home. So weird, huh? Nope. Weird, odd, disturbing & "coincidences" becomes your way of dealing with a very twisted hacker that gains pleasure of doing this to naive, innocent people all the time. But think about dealing with the above frustrated scenario, day in and day out for over 2 years!! I almost have my sanity back (I think) since my Hacking Griefer seems to have moved on...mmm Stalking? Thru my cell still? Probably then again, maybe not. What's the twisted little phreak gonna do? Don't give a shit. More like (hopefully) he's moved on... Right in front of the big ass truck going 80mph. All I can say is at least now I have a great excuse whenever there is a 'real' fluke while I have my freedom back with technology ... "The Hacker did it" & guess what? I don't give a damn!! Ha! Whatever!! IIWII - Moving Forward. Enjoying technology the way I have been trying to since way before I moved from MD, when 'Sherman' was on the prowl just waiting for just the right person to target... Who's next? I wonder how often the 'twilight zone' I encountered, has been reported by others? I seriously hope the hacker isn't attempting at this moment to make someone else questioning their sanity... I think being able to reverse IP's & zoom in on a hacker's location just might have something to do with my new found freedom. I love Apple!! But what I really want to know is... Why the hell did my Twitter account get suspended? >>>> guess I'll never know when I contacted @support they never really explained why, just that they were sorry & I had to guarantee that I had, in fact, read ALL their rules... Yea... Unhuh - RIGHT!!! My Twitter was out of commission for about 2 full days. I'm up and running again now & think I have around 1,500 Followers... So exciting!!! I was so fricken clueless, but I'm getting there. Follow me on Twitter @StalkedByHacker! And tweet me. Let's ROLL : )))
Monday, June 25, 2012
Don't become a victim of CYBER TERROR
It's something so many people just take for granted... Ahhh being able to share my story after so many failed attempts because I have finally regained (for now) enough freedom to get my story out about a Hacker that has made my life pure Hell. Trust me on this, if it happened to me, anyone's a target to the kind of Hacker that thrives off of causing you nothing but excruciating Grief by compromising everything you use through technology... PCs, Printers, Cell phones, LAN line etc. I have dealt w/ local police, CyberCrime Unit & the FBI in 2 different states in which they all believed the 'unbelievable' actions of a hacker who hacked his way into my Dell laptop in the safety of my home, and they all over sympathized with the Hell I was constantly being subjected to but to my astonishment there was no law the hacker actually broke!?!? Really? I'm pretty sure it's common knowledge that Hacking IS illegal when one obsesses that CYBER TERROR is acceptable in our world today!!? Corrupting every computer and printer you use is controlled by someone else to only corrupt it beyond repair... Can't possibly be okay! I just regret that I LET MY hacker -Sherman- hack his way into my Dell & eventually appear right before my eyes in April 2010 as a profile named Sherman w/ the Chess player icon & stole Administrative Rights, compromised the 2 emails that I was no longer able to access... THEN remote accessed the Dell & shortly after remote accessed my cell which was TOTALLY unacceptable!!! What about my Rights? What if it was you? And sadly it only got worse and the REAL nightmare was just beginning... the CYBER TERROR you could only perceive logical even if exposed to it in a horror movie you would still NEVER believe. Well, all I am trying to do is make people aware that Hacking Griefers do exist and you don't want to be subjected to so much misery that it almost destroys you! LITERALLY. A different form of CYBER BULLYING but with a genius(es) whose mission IS to destroy you to such a degree of questioning your own sanity; your interactions w/ technology will never be same if you let the Hacker gets his way... paranoia will begin to literally suffocate you... Share my story. Although people hear about 'hacking' on the news everyday (and it seems they always 'catch' the bad guy) well I am here to tell you - you do not want to be the one desperately trying to find the right resources that can FINALLY give you back your peace of mind. I utitlized every resource out there to only find out that Hacking Griefers are allowed to invade your life in such an intrusion way that unless subjected to it there is no way for 'others' to understand. Most people take it for granted, the freedom that everyone deserves to have using technology in our rapid growing high tech world unless you have a stalking hacker who gains pleasure thinking their prey is a game piece turned virtual. A bunch of phreaks playing a game, hiding behind technology and invading MY Cyber space since 2010 should be ILLEGAL. Just thank God for Apple and my beliefs... The next 'virtual game piece' may not be so lucky.
Labels:
Arin,
bully,
Connection,
crime,
Cyber,
Cybercrime Unit,
FBI,
Griefer,
hacker,
high-tech,
illegal,
legal,
network,
new technology,
phreaks,
police,
stalked,
Stalking
Saturday, May 26, 2012
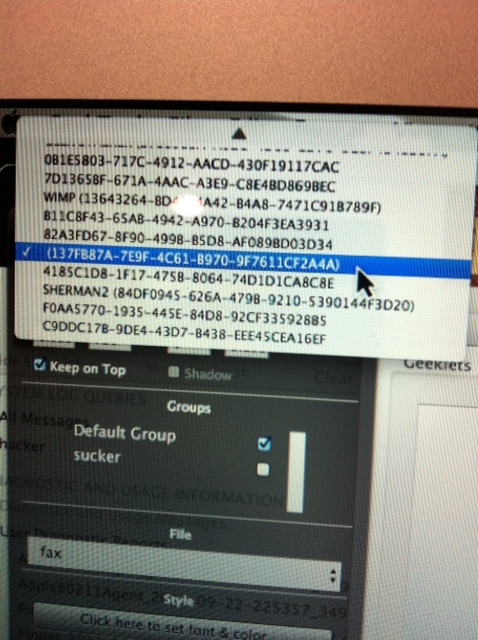
The Mystery GeekTool App & My Relentless Hacker
Pictures 2, 3, 4, 5, 6 & 8 - mystery App that no one is claiming to have put on my MacBook Air - The GeekTool App. Other pics show my Hacking Griefer's 'autograph' so boldly added once again as a User Profile on my Mac. When my 3 emails that were already built into the mail client & working just fine generated an error stating 'password rejected' right after I had been asked by an Apple Senior Advisor to send them the 'odd' logs I had created on my new MacBook Air & my network connection had been compromised, I knew for a fact that my hacker HAD been stalking me from my 1st connection and decided fervently to change everything I could in this App. Picture 5 is showing one of the icons I clicked on in this App that exposed 3 property values at first that apparently the hacker had built in (at the time I thought it was a built in Apple App & I knew what I was about to do could possibly whack out my Mac) but I added 3 fictitious values & unchecked everything checked & vis-a-versa then changed ISO Settings to ISO 2022 Japanese but I couldn't believe the property values just kept multiplying! What the hell is going on? By pure luck ALL my emails (over 10) that I was unable to use because of 'wrong UN or Password' populated from ALL devices; iPad, iPhone etc. & I lost ability to do anything because I no longer had Admin Rights on my MacBook Air. I clicked around & stumbled across 'Sherman' as a User Profile which was my Hacker's way of telling me he was still stalking me which I already knew because of all the bizaar encounters I had been having on everything to do with technology since Sherman first appeared on my Dell in April 2010 when I lived in MD. I have since moved to FL when the hacking Griefer appeared a 2nd time as Sherman in October 2011 but has made his presence very transparent until I started dealing with the FBI in MD in August & then shortly after my move from MD to FL in Sept. 2010 again with my LG Android Cell & my then brand new Lenovo laptop which kept acting strangely then getting corrupted time and time again. I thought I would have been safe since the remote accessing of my cell abruptly stopped shortly before I moved from MD. I had already stopped using my Dell completely after watching it delete pixel by pixel while on the phone with 'technical support' one night until about 4:30a.m in April 2010. When I woke up and literally jumped out of bed the next day around 3pm, I went to check my LAN line's VM & caller ID that 'technical support' was supposed to have made a follow up call around 11:00am and saw I had not received any calls and to my astonishment I had no dial tone NOR was I able to make or receive any calls on my cell either. I was completely terrified... in fear for my life. Everything that had led up to the time is incomprehensible. Was it my imagination or did I in fact talk to a REAL 'technical support' from Comcast that kept passing the buck and just made matters worse and never called me the following day. Right before my Dell started erasing, my hacker, named Sherman was in fact waving my present address at the time up and down the side of my screen as if on a newspaper clipping - Really?? Absolutely!!! A scare tactic on the Hacker's part to let me know he knew exactly where I lived... And many more similar haunting stunts. Then I overslept and and I had no way of making a phone call! How could my cell phone AND LAN line both NOT work at the same time? My heart was racing. Too scared to look at my Dell. I had to get to a pay phone or find the closest police station. That's when the reality of finding a pay phone were far and few in between. Hmmmm - I had never noticed that before... But I had never needed a pay phone where I was living before this terrifying incident & what had led up to it. Let me give some advice. Don't EVER go into a police station (or anywhere for that matter) unless you are somewhat composed and can talk rationally. But damn it I truly was in fear for my life. When you get subjected to Cyber Terror the last thing you're thinking is 'act normal' even though the reality as you once knew it, no longer exists and it's very difficult to be rational. At the time I questioned my physical well being. But trust me, I will never forget how I got treated in that police station in the dark of night as if I were same crazed out drug junkie! I was mortified but looking back I should have tried to collect myself a little bit before expecting the police to take what I had to say seriously. When I went to the police here in FL much calmer, the reaction was quite thankfully different. The only information I could get from the police in MD (my very first attempt of numerous attempts going to authorities) was to go on-line to www.ic3.gov and report the crime. No way! Seriously? How much sense did it make for them to tell me to go on-line when I clearly (not rationally maybe) explained amongst being in fear of my life & all the interactions I could think of at that frazzled time including someone was remote accessing my computer & controlling what I could do & not do. A library perhaps... that's another story. What part didn't they get? Just the beginning of 'pass the buck'. I knew after leaving the police trembling (who are supposed to protect but 'whatever'... ) the only place I would have felt safe at would be my Dad's house which was about 40 miles away. Had to find a damn pay phone! Thank God! My Stepmother answered - it didn't go to VM! And they had a computer. All I wanted at that point was to get a good night sleep. I would attempt as soon as possible to go to www.ic3.gov but not that night! BUT... There was only one major problem. The most unimaginable would soon slap me in the face blindfolded! To compound my baffled state of mind... The hacker was waiting for me... No I left my Dell at my house and haven't touched it since except about 3 weeks after my deranged escapade I took one quick glance thinking I would just see a blank screen since it was slowly erasing pixel by pixel when I last had my eyes on it with pure exhaustion talking to Comcast 'technical support'. Still waiting on that follow up call. NOT! But when I glanced at it I couldn't believe what I saw! My entire desktop was covered with newly named folders in alphabetical order and one of them had my X-husbands name on it (his name had kept appearing on my screen really tiny like it was far away in my screen then would float toward me magnifying slowly) Nope. Didn't click on a thing; was shocked to have seen anything at all. Turned it off, closed it and put it in its case - some authoritative figure may want to look at it and has actually been mentioned by CCU but I still have it in the case to this day; untouched since that bizarre encounter. As I mentioned, my hacker the Griefer who goes by Sherman knew somehow I would be attempting to report online the Cyber Terror to Cybercrime Unit from my parent's computer... Would I be able to? No!!! Another blog.
Take all precautions on your computers. Be safe. Don't think it can't happen to you!!! STOP CYBER TERROR!! How in God's name was 'my' hacker able to continue tormenting from my parent's house? How fricken whacked out.. He got into my PC so far away from my parents. No logic exists... The hacker was Stalking me to a degree - no one could imagine.
Take all precautions on your computers. Be safe. Don't think it can't happen to you!!! STOP CYBER TERROR!! How in God's name was 'my' hacker able to continue tormenting from my parent's house? How fricken whacked out.. He got into my PC so far away from my parents. No logic exists... The hacker was Stalking me to a degree - no one could imagine.
Labels:
App,
Apple,
bully,
compromised,
Computer,
Connection,
crime,
Cyber,
Cybercrime,
Dell,
FBI,
GeekTool,
Griefer,
hacked,
hacker,
illegal,
MacBook Air,
new technology,
phreaks,
Terror
Subscribe to:
Posts (Atom)